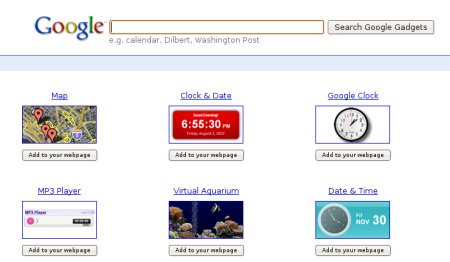
Black Hat presenters [Robert “RSnake” Hansen], CEO of SecTheory, and [Tom Stracener], security analyst at Cenzic, criticized Google in their presentation “Xploiting Google Gadgets”. [Hansen] and [Stracener] say that there’s currently no way for Google to confirm whether Google Gadget creations contain malicious content or not; this leaves the application vulnerable to a wide range of hacking ugliness such as data poisoning, worms, and theft of data. [Hansen] himself isn’t exactly on the friendliest terms with Google. He’s got a bit of a contentious history and he claims that Google has threatened legal action against him. Nevertheless, if what was presented is true and accurate, then Google has a huge security issue that needs to be addressed sooner rather than later. Google has not yet commented on the situation.
Year: 2008
Black Hat 2008: What’s Next For Firefox Security

Black Hat 2008: French Hacking Failure

French reporters at Black Hat crossed the line when they sniffed fellow reporters’ login info on the designated “safe” wired network. Proud of their handiwork, they were nabbed when they tried to get their spoils posted on the wall of sheep, which is used to publicly post attendees credintials. It turns out that monitoring communications without informing one of the parties involved is a felony, so although it is legal to sniff convention goers’ login info with their knowledge, hacking reporters covering the event is a no-no. An FBI agent we ran into commented that in his experience, they’d probably just turn it over to the local US attorney’s office to see if they wanted to proceed with an investigation.
We’re in the Defcon press room today and there’s still a buzz about these “sleazy” French reporters. We’re tunneling through our cell connection like any sane person at a security conference.
USB Wall Charger

[rbhays] did this sweet little hack back in 2006. He took a Motorola cellphone wall charger and modified it into a USB wall charger. He needed to charge his iPod, but misplaced the original charger. A replacement would have cost him $30. So he did what any respectable hacker would do, he cut up something else to make it work for him.
He had one sitting around that was equipped with a mini USB end. He checked it out and it was the perfect voltage. Some commenters below the project noted that their motorola charger had a higher voltage rating than his. Those would still work, but would require some extra steps to bring the voltage down.
After some careful soldering, and a bit of super glue, he’s left with a perfectly good wall charger. He can charge most things that only use the juice from the wall. Some things refuse to charge though, such as Zunes. There was another project by [Cvesey] that claims to charge Zunes as well. While wall chargers may be available fairly cheaply now, many of us have some of these cellphone chargers just sitting around. Now we have a use for them.
New E-Passports Cloned
Within an hour, Jeron Van Beek was able to create a successful clone of Britain’s new E-Passport. All he needed was a £40 card reader, two £10 RFID chips, and a small, improvised script. Although the exact details were not specified, it looks like he read the ID on the real passport using the RFID reader, then he wrote it to the two blank chips and put them in the fake passports. There is also a flaw which may allow outright forging of the passports. Nearly all of the 45 countries using the system have not yet registered with the Public Key Directory, which was put in place to make forging impossible.
The government is claiming that this hack is a hoax, but recent reports have shown that these RFID systems were never secure. No matter what the actual truth is about these hacks, it can certainly be said that the ability to clone or forge these passports would be a devastating security issue for every country involved.
[Photo: Digital World Tokyo]
[via The Guardian]
Homeland Security Issues Policy On Laptop Seizures

The US Department of Homeland Security recently disclosed a new policy that allows agents to seize laptops, or anything capable of storing information, “for a reasonable period of time”. Okay, so this seems normal; A government agency is declaring they may confiscate personal property. However, the strange part of this story is that under this policy, federal agents can confiscate these things without any suspicion of wrong doing or any reason what so ever. So what happens to your personal data after they seize your laptop? Apparently they share the data with federal agencies, and in some cases the private sector, as additional services such as file decryption or translation are needed. While this may seem like a major violation of privacy, it is important to note that this policy only applies to people entering the United States. However given the direction that our federal government is moving in the area of security, it wouldn’t surprise me if this policy will soon apply for domestic flights as well.
[photo: postmodern sleaze]
[via eff.org]
Hacking Pleo For Face Recognition And Remote Control

GRIP, the Group for Interdisciplinary Psychology at the University of Bamberg have put together a couple tutorials on hacking the Pleo. For those unfamiliar, the Pleo is a small robot shaped like a dinosaur. Their goal was to make it cute and simulate emotion at a higher level than previously attained by consumer robots. Ugobe, the makers of Pleo encourage hacking of the unit and the controlling software. Look at the “developers” area of their site to download all kinds of tools to work on your Pleo.
The two tutorials released by GRIP cover adding wireless communication with a PC and adding a higher resolution camera to the unit. The goal was to make the platform capable of doing facial recognition.
Continue reading “Hacking Pleo For Face Recognition And Remote Control”










