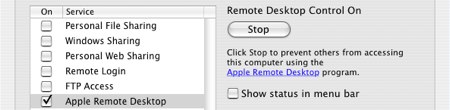
Yesterday, Slashdot reported a privilege escalation vulnerability in OSX. Using AppleScript you can tell the ARDAgent to execute arbitrary shell script. Since, ARDAgent is running as root, all child processes inherit root privleges. Intego points out that if the user has activated Apple Remote Desktop sharing the ARDAgent can’t be exploited in this fashion. So, the short term solution is to turn on ARD, which you can do without giving any accounts access privileges. TUAW has an illustrated guide to doing this in 10.4 and 10.5.
Month: June 2008
Wiretapping And How To Avoid It
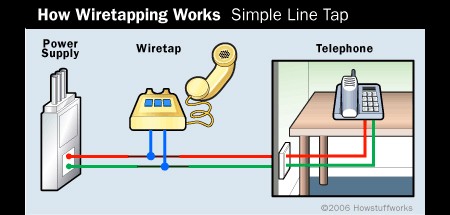
No matter who you suspect is plotting your doom, you’ll need need to know the way wiretapping works in order to learn their plans and shield yourself from their surveillance. Luckily, ITSecurity has posted a comprehensive
article about wiretapping, including information on how to wiretap and how to find out if someone is wiretapping you.
One of the more intriguing methods of wiretapping the articles discusses is a service by a company called FlexiSPY. It works by covertly installing a program onto the target’s cellphone. Once installed, the spying party can listen to anything going on in the room the target is in by calling the phone. It won’t ring, vibrate, or give any indication that it is transmitting audio data.
Some of the more hack-oriented methods involve tapping into a landline, using special software to record VoIP calls, or buying a wiretapping kit. Of course, countermeasures, are also discussed, but some of the links they provide are a little more informative on the topic of defense against wiretapping.
Check Washing Vulnerabilities

[vector] sent in some of his other work, but I found his posts(part 1, part 2, part 3 and final thoughts) on check washing experiments pretty interesting. His results should be enough to make you think twice about writing checks. He tested a few different pens and tested them on real check using Acetone and Alcohol as solvents.
The Price Of His Toys Returns

We’re big fans of scratch built transportation and got some great news earlier this month: After a long hiatus, thepriceofhistoys.com has returned and is ready to serve up all the news about kit cars and home-built cars that you could want. For those who don’t know, kit cars are sets of car parts that require assembly often lacking drivetrain components, which must be acquired from donor vehicles. Aside from kit cars, home-builds, and the occasional custom job, many of the cars the site discusses are also for sale.
Kit cars can be pretty fun on their own, but many of the builds featured on the site spice it up further by adding varying levels of customization. This Tornado McLaren M6 GTR Replica, for example, uses a 3.5L V8 Rover engine and some custom body work to improve visibility. Another fascinating and rare kit uses a Beetle’s chassis and features a body that looks like a Beetle crossed with a Porche. Of course, none of these are as practical cutting a Geo Metro in half for improved milage, but to car kit builders, practicality holds a very low place on their list of priorities.
DecaffeinatID: Simple Security Log Monitor
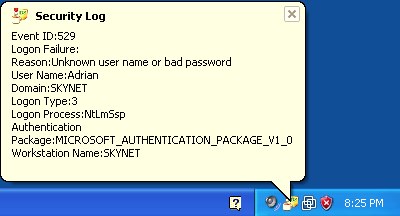
Irongeek put together a simple program for monitoring network shenanigans when you’re on an untrusted network like the coffee shop. It sits in the Windows Systray and notifies you about a variety of events. It alerts you when it sees the MAC address of the IP gateway change. It watches the security log and warns you of any attempted or successful logins. The firewall log is also monitered. Try it out and send him any bug reports/feature requests you might have.
Hardware FAIL
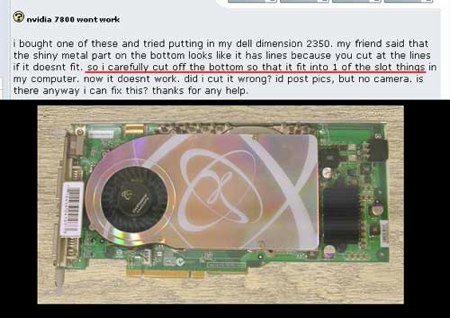
This forum post from 2005 has us at a loss for words. Please educate your loved ones. Only you can prevent senseless hardware mutilation.
[via PhotoBasement]
Atari 7800 Portable

Ben Heck has just wrapped up his latest project, a portable Atari 7800. He had meant to do this a long time ago, but lacking experience, the complex looking circuit board scared him off. It features a seven inch display, rechargeable batteries, combination driving and paddle controllers, plus AV out. The console was built by request and just like his other pojects: he’s not shy about showing you how it’s put together. Look for a making-of coming soon.










