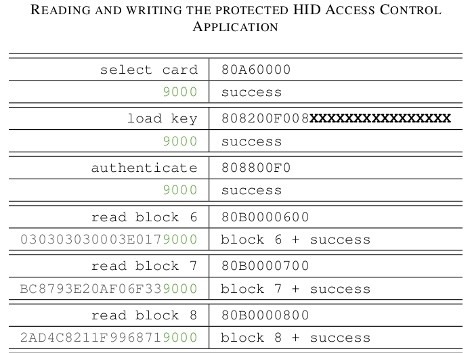
A system is only as strong as its weakest link and [Roberto Barrios] found that on the sixth generation iPod nano the buttons are the problem. It makes sense that the buttons would be exposed to wear since they’re movable parts. The issue isn’t one of contacts or springs wearing out, but how the buttons are assembled. Each consist of a couple of parts; the tactile piece that you see and press, the electrical switch which converts that force into an electrical signal, and a shim that bridges the gap between the two.
After two months of use the iPod [Roberto] was fixing had stopped responding to presses of the Power button. It turns out that the shims are attached with double-sided tape. Inspection of the internals revealed that the shim had slid to one side and no longer made contact with the electrical system. His solution was to remove the tape and clean off the goo, then reattach the shims using “two-part metal cement”.
With the shim back in place all is well but he made sure to execute this fix on all of the buttons before reassembly.