FireEye just put out a report on catching the Russian hacker group “Advanced Persistent Threat 29” (APT29, for lack of a better code name) using the meek plugin for TOR to hide their traffic. If you’re using meek with meek-reflect.appspot.com, you’ll find it’s been shut down. If all of this is gibberish to you, read on for a breakdown.
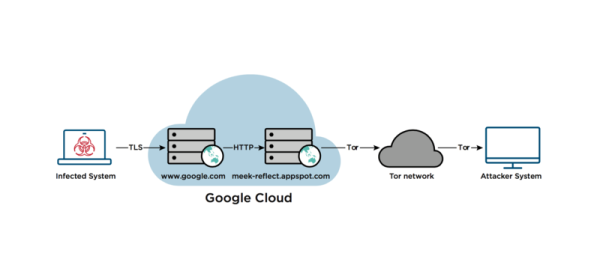
meek is a clever piece of software. Imagine that you wanted to communicate with the Tor anonymizing network, but that you didn’t want anyone to know that you were. Maybe you live in a country where a firewall prevents you from accessing the full Web, and blocks Tor entry nodes as part of their Great Firewall. You’d want to send traffic somewhere innocuous first, and then bounce it over to Tor, in order to communicate freely.
That’s what meek does, but it goes one step further. The reflector server is hosted using the same content-delivery network (CDN) as a popular service, say Google’s search engine. The CDN has an IP address, like every other computer on the Internet, but it delivers content for any of the various services it hosts. Traffic to the CDN, encrypted with TLS, looks the same whether it’s going to the meek reflector or to Google, so nobody on the outside can tell whether it is a search query or packets destined for Tor. Inside the CDN, it’s unencrypted and passed along to the reflector.
Anyway, meek was invented to help bring the uncensored Internet to people who live in oppressive regimes, and now cybersecurity researchers have observed it being used by Russian state hackers to hide their tracks. Sigh. Technology doesn’t know which side it’s on — the same backdoor that the FBI wants to plant in all our communications can be used by the mafia just as easily. Plugins that are meant to bring people freedom of speech can just as easily be used to hide the actions of nation-state hackers.
What a strange world we live in.