Laptop chargers face a hard life. They’re repeatedly plugged and unplugged, coiled up, stuffed into bags, thrown around, and just generally treated fairly poorly. Combine this with fairly lightweight design and it’s not uncommon for a laptop charger to fail after a few years. It’s usually the connector that goes first. Such was the case when I found myself face to face with a failed Macbook charger, and figured it’d be a simple fix. Alas, I was wrong.
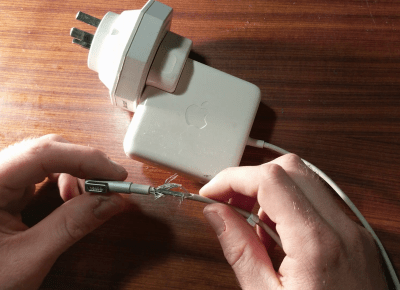
Unlike most PC manufacturers, who rely on the humble barrel jack and its readily available variants, Apple liked to use the Magsafe connector on its Macbook line. This connector has many benefits, such as quick release in the event someone trips over the cable, and the fact that it can be plugged in without regard to orientation. However, it’s not the easiest to fix. When the charger began failing, I noticed two symptoms. The first was that the charger would only function if the cable was held just so, in exactly the right orientation. The other, was that even when it would charge, the connector would become very hot. This led me to suspect an intermittent connection was the culprit, and it was quite a poor one at that; the high resistance leading to the heat issue.
It’s at this point with any other charger that you get out your trusty sidecutters, lop the end off, and tap away at Digikey to get a replacement part on the way. With Magsafe? No dice. Replacement parts simply aren’t available — a common problem with proprietary connectors. I endeavoured to fix the problem anyway. I began to strip away the metal shell around the back of the connector with my sidecutters, and eventually an angle grinder. A Dremel would have been the perfect tool for the job, actually, but I persevered regardless. After much consternation, I had the connector peeled back and was able to identify the problem.
Continue reading “Repairing A Macbook Charger… With A Pistachio Nut”