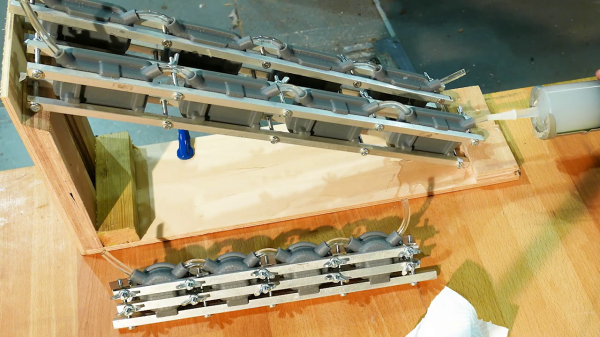
The techniques for making single-digit quantities of custom molded parts don’t scale well when you need to make dozens, as [Kevin Holmes] discovered. He needed to make 80-some sets of a silicone motor mount, and the one-up mold process was not going to work. He explores several solutions, which he rejects as being too complicated. Finally [Kevin] comes up with the idea of daisy-chaining banks of molds clamped together with rails of stock metal bars. It’s a pretty nifty process to watch and you can check the video out below, which is not unlike a very slow 7495 four-bit shift register.
Even though the silicone he uses is clear, pay attention and you can still see the carry-out as it propagates from mold to mold. He manually performs the nibble carry operation from one bank to the next — we wonder if he could cascade these banks, and inject all 80 in one really big squeeze?
Why would someone need 80 sets of silicone rubber motor mounts, you may ask? Well, you may remember the 4-mation 3D zoetrope that we wrote about back in 2018. [Kevin] is one of the founders of this mesmerizing project, and it would seem that their Kickstarter project has been successful. As he demonstrates in the video below, without some type of noise dampening mounts, a rumble from the motor is amplified through the stage of the zoetrope. If you have any favorite mold-making tips for small batch manufacturing, let us know in the comments below. Thanks to [George Graves] for sending this tip our way.