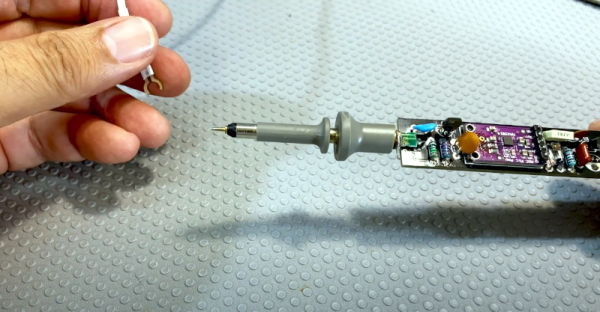
[Electronics Old and New] has a new version of one of his old projects. The original project was an active probe. He took what he learned building that probe and put it into a new probe design. He also added automatic gain control or AGC. You can see a video explanation of the design below. The probe is essentially a high-impedance input using a JFET that can amplify audio or demodulated RF signals, which is a handy device to have when troubleshooting radios.
The audio amplifier is a simple LM386 circuit. The real work is in the input stage and the new AGC circuit. Honestly, we’ve used the amplifier by itself for a similar function, although the raw input impedance of the chip is only about 50K and is less in many circuits that use a pot on the input. Having a JFET buffer and an RF demodulating diode is certainly handy. You’d think the AGC block would be in the audio stage. However, the design uses it ahead of the detector which is great as long as the amplifier can handle the RF frequency you are interested in. In this case, we think he’s mostly working on old tube AM radios, so the max signal is probably in the neighborhood of 1 MHz.

The module is made to amplify an electret microphone using a MAX9814 which has AGC. The module had a microphone that came off for this project. The datasheet doesn’t mention an upper frequency limit, but a similar Maxim part mentions its gain is greater than 5 at 600 kHz, so for the kind of signals this is probably used for, it should work well. We wondered if you could use the module and dispense with the JFET input. The chip probably has a pretty high input impedance, but the datasheet doesn’t give a great indication.
For years we used a signal tracer from Radio Shack which — if we could still find it — now has an LM386 inside of it after the original electronics failed decades ago. In those days, fixing an AM radio involved either using a device like this to find where you did and didn’t have a signal or injecting signals at different points in the radio. Two sides of the same coin. For example, if you could hear a signal at the volume control — that indicated the RF stages were good and you had a problem on the audio side. Conversely, if you injected a signal at the volume control, not hearing would mean the same thing. Once you knew if the problem was in the RF or AF side, you’d split that part roughly in half and repeat the operation until you were down to one bad stage. Of course, you could use signal generators and scopes, but in those days you weren’t as likely to have those.
Heathkit, of course, had their own version. It even had on of those amazing magic eye tubes.