It’s easy to become jaded by modern microcontrollers: for just a few bucks you can get a MCU that’s powerful enough to give a desktop computer from the early 90s a run for its money while packing in contemporary technology like WiFi and Bluetooth. For many projects we don’t even have to consider optimizing our code, because we aren’t even scratching the surface of what the hardware is capable of.
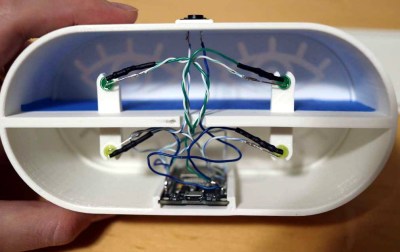
But sometimes you don’t have the luxury of using the latest-and-greatest chip, and have to play the hand you’re dealt. That’s when folks like [Larry Bank] really shine. In a recent write-up, he goes over his experiments with driving e-paper displays (specifically, salvaged electronic shelf labels) with 8-bit MCUs that on paper shouldn’t have the resources to run them.

The problem is that these displays generally expect to be handed a fully-formed image, which can easily exceed the free RAM on a low-end chip. For example, a 1-bit 128 x 128 image would consume 2 KB of RAM — more than four times the available memory on an ATtiny85.
As [Larry] explains, his alternate approach is to write data to the display in columns that are only one byte wide. Combined with his existing work with image decompression on constrained hardware, he’s able to rapidly draw out full-screen TIFF images using an Arduino UNO as demonstrated in the video after the break. He hopes the work will inspire others to experiment with what’s possible using the dinky MCUs you generally find in second-hand shelf labels.
Continue reading “Driving E-Paper Displays With Memory Limited MCUs”