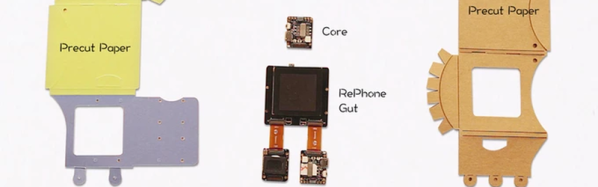
If you’ve spent much time tinkering with electronics, you’ve probably heard of [Seeedstudio] from their development boards, tools, and their PCB fabrication service. Their latest Kickstarter venture is the RePhone, an open source and modular cell phone that will allow hackers to put together a phone by blending GSM modules, batteries, screens, and other stock units, including an Arduino-based processing core, GPS, NFC, and other building blocks.
The funding campaign has already exceeded its goal and delivery is scheduled for next year with a basic kit weighing in at a projected $59, according to [Seeed]. Presumably, the core phone module will have regulatory acceptance, but the other ancillary modules won’t require as rigorous testing and certification.
What would you do with an inexpensive, embeddable cell phone? The modules are tiny, so you could implant them in lots of places. Some of [Seeed’s] more interesting ideas include building a phone into a walking stick, a dog collar, or a kite (although we were thinking quadcopters).
Of course, we’ve seen GSM and cell phone shields for Arduino before. Difficult to imagine sticking those in a dog collar, though, unless you have a fairly large dog. If you are a fan of 1960’s TV, it is easy to imagine a better shoe phone or a working Star Trek communicator.