If you have a reasonable home theater setup in your living room, odds are you have up to half a dozen remotes sitting around. Short of trying to get your cable receiver’s remote to control everything or laying down some cash for a Harmony remote, what’s a hacker to do?
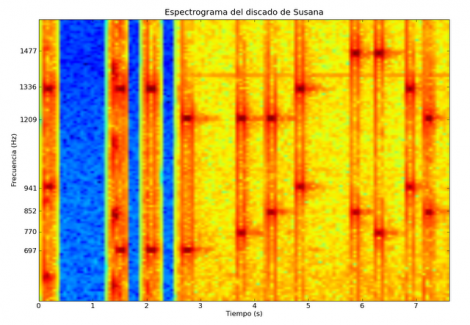
[Andrey] decided he wanted to use his iPhone as a universal IR remote, but he didn’t want to pay very much to do so. Instead of buying a dongle at the store, he soldered some IR LEDs to an old headphone plug, creating a mini IR dongle to control his equipment. After studying IR signaling a bit, he got to work encoding IR remote commands into wav files using Python. The files are then played on his iPhone, allowing him to submit certain commands to his TV set.
Unfortunately, the process of manually converting IR codes to audio files doesn’t quite seem like the most efficient way of doing things. There are other IR dongles currently on the market that utilize the headphone jack, most of which provide pretty robust software for free. These might make a good alternative to manually creating audio files for each IR command. We honestly haven’t seen any teardowns of these retail IR dongles posted online, but it would be interesting to see how they compare to what [Andrey] has put together.