If you ever needed proof that class-action lawsuits are a good deal only for the lawyers, look no further than the news that Tim Hortons will settle a data-tracking suit with a doughnut and a coffee. For those of you who are not in Canada or Canada-adjacent, “Timmy’s” is a chain of restaurants that are kind of the love child of a McDonald’s and a Dunkin Donut shop. An investigation into the chain’s app a couple of years ago revealed that customer location data was being logged silently, even when they were not using the app, and even far, far away from the nearest Tim Hortons. The chain is proposing to settle with class members to the tune of a coupon good for one free hot beverage and one baked good, in total valuing a whopping $8.68. The lawyers, on the other hand, will be pulling in $1.5 million plus taxes. There’s no word if they are taking that in cash or as 172,811 coffees and doughnuts, but we think we can guess.
Hackaday Columns4663 Articles
This excellent content from the Hackaday writing crew highlights recurring topics and popular series like Linux-Fu, 3D-Printering, Hackaday Links, This Week in Security, Inputs of Interest, Profiles in Science, Retrotechtacular, Ask Hackaday, Teardowns, Reviews, and many more.
Learning By Playing
Summer break has started over here, and my son went off to his first of a few day-camp-like activities last week. It was actually really cool – a workshop held by our local Fablab where they have the kids make a Minecraft building and then get to 3D-print it out. He loves playing and building in Minecraft, so we figured this would be right up his alley.
I had naively thought that it would work something like this: the kids build something in Minecraft, and then some software extracts the build and converts it into an STL file. Makes sense, because they already are more-or-less fluent in Minecraft modelling. And as I thought about that, it was a pretty clever idea.
But the truth was even sneakier. They warmed up by making something in Minecraft, then they opened up TinkerCAD, which was new to all of the kids, and built a 3D model there. Then they converted the TinkerCAD models into Minecraft, and played with what they had just built while the 3D printers hummed away.
The kids didn’t even flinch at having to learn a new 3D modelling tool, and the parallels to what they were already comfortable doing in Minecraft were obvious to them. My son came home and told me how much easier it was to do your 3D modelling in “this other Minecraft” – he meant TinkerCAD – because you don’t need to build everything out of single blocks. He thought he was playing games, but he’d secretly used his first CAD tool. Nice trick!
Then I look back and realize how much I must have learned about computers through playing as a kid. Heck, how much I still learn through playing. And of course I’m not alone – that’s one of the things that shines through in a large number of the projects we feature. Hack on and have fun!
Hackaday Podcast 180: Tiny CRTs, Springy PCBs, And Measuring Trees

This week, Editor-in-Chief Elliot Williams and Assignments Editor Kristina Panos traded sweat for silence, recording from their respective attic-level offices in the August heat unaided by fans (too noisy). We decided there’s no real news this week that lacks a political bent, except maybe that Winamp is back with a new version that’s four years in the making. (Is Winamp divisive?) Does it still whip the llama’s ass? You be the judge.
After Elliot gives Kristina a brief math lesson in increasing area with regard to 3D printer nozzle sizes, we talk a bit about 3D pens, drool over a truly customizable macropad that uses a microcontroller for each keyswitch, and discuss dendrometers and tree health. Then it’s back to keyboards for one incredible modular build with an e-ink display and haptic feedback knob which is soon to go open source.
Finally, we talk tiny CRTs, a USB drive that must have the ultimate in security through obscurity, discuss the merits of retrograde clocks, and wonder aloud about the utility of jumping PCBs. Don’t bounce on us just yet — not until you hear about our first electronics wins and learn the one thing Kristina doesn’t do when she’s spending all day in the heat.
Direct download. And listen with Winamp!
Check out the links below if you want to follow along, and as always, tell us what you think about this episode in the comments!
Continue reading “Hackaday Podcast 180: Tiny CRTs, Springy PCBs, And Measuring Trees”
This Week In Security: Symbiote Research And Detection, Routing Hijacks, Bruggling, And More
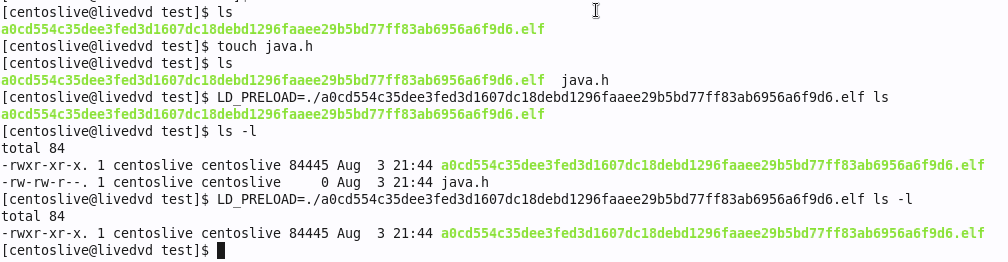
Last week we covered the Symbiote Rootkit, based on the excellent work by Blackberry, Intezer, and Cyber Geeks. This particular piece of malware takes some particularly clever and devious steps to hide. It uses an LD_PRELOAD to interfere with system libraries on-the-fly, hiding certain files, processes, ports, and even traffic from users and detection tools. Read last week’s column and the source articles linked there for the details.
There is a general technique for detecting rootkits, where a tool creates a file or process that mimics the elements of the rootkit, and then checks whether any of the fakes mysteriously disappear. In reading about Symbiote, I looked for tooling that we could recommend, that uses this technique to check for infections. Coming up short, I dusted my security researcher hat off, and got to work. A very helpful pointer from Intezer led me to MalwareBazaar’s page on Symbiote. Do note, that page hosts live malware samples. Don’t download lightly.
This brings us to the first big problem we need to address. How do you handle malware without getting your machine and wider network infected? Virtualization can be a big part of the answer here. It’s a really big leap for malware to infect a virtual machine, and then jump the gap to infect the host. A bit of careful setup can make that even safer. First, use a different OS or distro for your VM host and research client. Sophisticated malware tends to be very targeted, and it’s unlikely that a given sample will have support for two different distros baked in. The bare-metal host is an up-to-date install for best security, but what about the victim?
While we want a bulletproof foundation, our research VM needs to be vulnerable. If the malware is targeted at a specific kernel version or library, we need that exact version to even get started. Unfortunately the samples at MalwareBazaar don’t include details on the machine where they were found, but they do come with links off to other analysis tools, like Intezer Analyze. One particular embedded string caught my eye: GCC: (GNU) 4.4.7 20120313 (Red Hat 4.4.7-17) That’s likely from the machine where this particular Symbiote sample was compiled, and it seems like a good starting point. GCC 4.4.7-17 shipped with Red Hat Enterprise Linux version 6.8. So we grab a CentOS 6.8 live DVD ISO, and get it booting on our VM host.
The next step is to download the malware samples directly from MalwareBazaar. They come in encrypted zips, just to make it harder to accidentally infect yourself. We don’t want those to land anywhere but the intended target. I went a step further and disconnected both the virtual network adapter and physical network cable, to truly air gap my research environment. I had my malware and likely target, and it was time to test my theory that Symbiote was trying too hard to be sneaky, and would sound the alarm on itself if I poked it just right.
Success! We’re using touch to create a file named java.h, and using ls to verify that it’s really there. Then, add the LD_PRELOAD and run ls again, and java.h is mysteriously missing. A similar trick works for detecting process hiding. We turn java.h into a script by writing while true; do sleep 1; done into it. Run the script in the background, and see if it’s listed in ps -A -caf. For a filename on Symbiote’s hide list, it too disappears. The best part is that we can script this detection. I give you, sym-test.sh. It creates and runs a simple script for each of the known Symbiote files, then uses ls and ps to look for the scripts. A Symbiote variant that works like the samples we’ve seen in the wild will give away its presence and be detected. If you find Symbiote on your machine via this script, be sure to let us know!
BGP Hijack — Maybe
There was a bit of BGP weirdness last week, where the Russian telecom company, Rostelecom, announced routing for 17.70.96.0/19. This block of IPs is owned by Apple, and all signs point to this being an unauthorized announce. BGP, the Border Gateway Protocol, is one of the most important network protocols you may not have heard of, and essentially carries the instructions on how to route internet traffic around the world. It’s also historically not had any security protocols baked-in, simply relying on good behavior from all the players. There is RPKI, a new standard for cryptographic signatures for routing updates, but it’s not a hard requirement and not widely deployed yet.
BGP, without any of the security enhancement schemes, works by honoring the most specific route available. Apple announces routes for 17.0.0.0/9, a network of over 8,000,000 IPs. Rostelecom started announcing 17.70.96.0/19, a much smaller subnet containing just over 8,000 IPs. The more specific route wins, and Rostelecom has a valid ASN, so the Internet made the routing shift. Someone at Apple was paying attention, and pushed a routing update for 17.70.96.0/21, moving what is presumably the most important 2,046 IPs back to their proper destination. After about 12 hours, Rostelecom dropped the bogus routes. Neither Apple nor Rostelecom have released statements about the incident.
Were this the first incident involving Rostelecom, it would be natural to conclude this was an honest mistake. Rostelecom has demonstrated bad behavior in the past, so the element of plausible deniability is waning. Could this have been part of a targeted operation against someone’s iPhone or Apple account? It’s hard to say whether we’ll be privy to the details any time soon. At the very least, you can watch a replay of the network carnage.
Email Routing Hijack
Cloudflare is expanding into email routing, and researcher [Albert Pedersen] was a bit miffed not to get invited into the closed Beta. (The Beta is open now, if you need virtual email addresses for your domains.) Turns out, you can use something like the Burp Suite to “opt in” to the beta on the sly — just intercept the Cloudflare API response on loading the dashboard, and set "beta": true. The backend doesn’t check after the initial dashboard load. While access to a temporarily closed beta isn’t a huge security issue, it suggests that there might be some similar bugs to find. Spoilers: there were.
When setting up a domain on your Cloudflare account, you first add the domain, and then go through the steps to verify ownership. Until that is completed, it is an unverified domain, a limbo state where you shouldn’t be able to do anything other than complete verification or drop the domain. Even if a domain is fully active in an account, you can attempt to add it to a different account, and it will show up as one of these pending domains. Our intrepid hacker had to check, was there a similar missing check here? What happens if you add email routing to an unverified domain? Turns out, at the time, it worked without complaint. A domain had to already be using Cloudflare for email, but this trick allowed intercepting all emails going to such a domain. [Albert] informed Cloudflare via HackerOne, and scored a handy $6,000 for the find. Nice!
Post-Quantum, But Still Busted
The National Institute of Standards and Technology, NIST, is running an ongoing competition to select the next generation of cryptography algorithms, with the goal of a set of standards that are immune to quantum computers. There was recently a rather stark reminder that in addition to resistance to quantum algorithms, a cryptographic scheme needs to be secure against classical attacks as well.
SIKE was one of the algorithms making its way through the selection process, and a paper was just recently published that demonstrated a technique to crack the algorithm in about an hour. The technique used has been known for a while, but is extremely high-level mathematics, which is why it took so long for the exact attack to be demonstrated. While cryptographers are mathematicians, they don’t generally work in the realm of bleeding-edge math, so these unanticipated interactions do show up from time to time. If nothing else, it’s great that the flaw was discovered now, and not after ratification and widespread use of the new technique.
Bits and Bruggling Bytes
A portmanteau of Browser and Smuggling, Bruggling is a new data exfiltration technique that is just silly enough to work. Some corporate networks try very hard to limit the ways users and malicious applications can get data off the network and out to a bad actor over the Internet. This is something of a hopeless quest, and Bruggling is yet another example. So what is it? Bruggling is stuffing data into the names and contents of bookmarks, and letting the browser sync those bookmarks. As this looks like normal traffic, albeit potentially a *lot* of traffic, it generally won’t trigger any IDS systems the way odd DNS requests might. So far Bruggling is just an academic idea, and hasn’t been observed in the wild, but just may be coming to malware near you.
LibreOffice just patched a handful of issues, and two of them are particularly noteworthy. First is CVE-2022-26305, a flaw in how macros are signed and verified. The signature of the macro itself wasn’t properly checked, and by cloning the serial number and issuer string of a trusted macro, a malicious one could bypass the normal filter. And CVE-2022-26306 is a cryptographic weakness in how LibreOffice stores passwords. The Initialization Vector used for encryption was a static value rather than randomly created for each install. This sort of flaw usually allows a pre-computation attack, where a lookup table can be compiled that enables quickly cracking an arbitrary encrypted data set. In up-to-date versions of LibreOffice, if using this feature, the user will be prompted for a new password to re-encrypt their configuration more securely.
Samba has also fixed a handful of problems, one of which sounds like a great plot point for a Hollywood hacking movie. First is CVE-2022-32744, a logic flaw where any valid password is accepted for a password change request, rather than only accepting the valid password for the account being changed. And CVE-2022-32742 is the fun one, where an SMB1 connection can trigger a buffer underflow. Essentially a client tells the server it wants to print 10 megabytes, and sends along the 15 bytes to print (numbers are fabricated for making the point). The server copies the data from the way-too-small buffer, and uses the size value set by the attacker, a la Heartbleed. I want to see the caper movie where data is stolen by using this sort of bug to print it out to the long-forgotten line-feed printer.
And finally, Atlassian Confluence installs are under active attack, as a result of a handful of exploits. There were hard-coded credentials left behind in the on-premise Confluence solution, and those credentials were released online. A pair of critical vulnerabilities in Servlet Filters are exploitable without valid credentials. If you’re still running unpatched, unmitigated Confluence installs, it may be time to jump straight to containment and cleanup. Ouch!
Reduced Sulfur Emissions Could Cause Climate Shock
When we talk about emissions these days, we typically talk about cutting them back for the good of the environment. However, the climate system is a complex beast, and one we’re still learning to understand.
As it turns out, cutting back on emissions may have unexpected or undesirable effects. Some scientists are concerned that cuts to human-induced sulfur emissions may actually be warming the Earth.
Continue reading “Reduced Sulfur Emissions Could Cause Climate Shock”
The Hackaday Summer Camp Survival Guide
It’s a feature of summer for us, the round of hacker camps in which members of our community gather in fields and spend a few days relaxing and doing what we do best. This summer I’ll have been to four of them by September, one of which was unexpected because a last-minute ticket came my way. For Hackaday they’re a chance to connect with our readers and maybe see come of the coolest stuff in person.
If you consult the wiki for your hacker camp of choice then you’ll usually find a page of tips about what to bring. Starting with a tent and a sleeping bag and probably going on to sunscreen, a hat, and maybe how to avoid dehydration. I’d probably add spare toilet paper and disinfectant spray in case the toilets are nightmarish. All very practical stuff, but expressed in a dry list format that doesn’t really tell you what to expect. A hacker camp can be overwhelming if you’ve not been to one before, so how do you get the best out of it? Here are a few tips based on our experience. Continue reading “The Hackaday Summer Camp Survival Guide”
Mutually Crafted Happiness: How MCH2022 Happened
Just a few days ago, MCH2022, a six day long hacker camp in Netherlands, has concluded – bringing about three thousand hackers together to hang out. It was my first trip to a large hacker camp like this, as I’ve only been to smaller ones, and this story is coming from someone who’s only now encountering the complexity and intricacy of one. This is the story of how it’s run on the inside.
 MCH2022 is the successor of a hacker camp series in the Netherlands – you might’ve heard of the the previous one, SHA, organized in 2017. The “MCH” part officially stands for May Contain Hackers – and those, it absolutely did contain. An event for hackers of all kinds to rest, meet each other, and hang out – long overdue, and in fact, delayed for a year due to the everpresent pandemic. This wasn’t a conference-like event where you’d expect a schedule, catering and entertainment – a lot of what made MCH cool was each hacker’s unique input.
MCH2022 is the successor of a hacker camp series in the Netherlands – you might’ve heard of the the previous one, SHA, organized in 2017. The “MCH” part officially stands for May Contain Hackers – and those, it absolutely did contain. An event for hackers of all kinds to rest, meet each other, and hang out – long overdue, and in fact, delayed for a year due to the everpresent pandemic. This wasn’t a conference-like event where you’d expect a schedule, catering and entertainment – a lot of what made MCH cool was each hacker’s unique input.
Just like many other camps similar to this, it was a volunteer-organized event – there’s no company standing behind it, save for a few sponsors with no influence on decisionmaking; it’s an event by hackers, for hackers. The Netherlands has a healthy culture of hackerspaces, with plenty of cooperation between them, and forming a self-organized network of volunteers, that cooperation works magic. Continue reading “Mutually Crafted Happiness: How MCH2022 Happened”