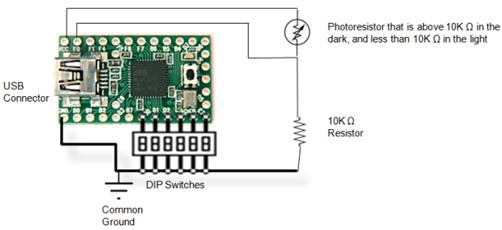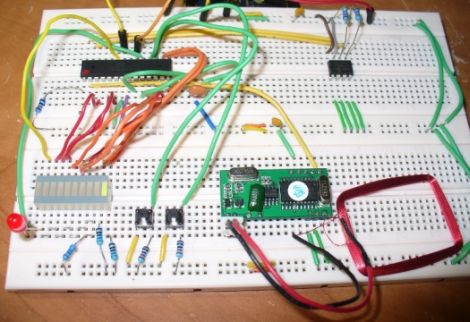
A few months back, [John] was reading an article about a simple RFID security system kit, and decided he would like to build one himself. While many of the system’s details, including full schematics were provided, he was dismayed to find that the source code for the project was not published as it was held under copyright by the manufacturer. Believing that open source is better, he modified the original design, replacing their PIC controller with an ATmega328 armed with an Arduino bootloader.
His system replicates all of the original kit’s functionality, while offering plenty of opportunity for modification beyond the initial design. The article contains a complete parts list, wiring schematic, and the Arduino code required to get things up and running. He even has a video of his clone at work, demonstrating the acceptance and rejection of RFID tags as well as the system’s learning mode.