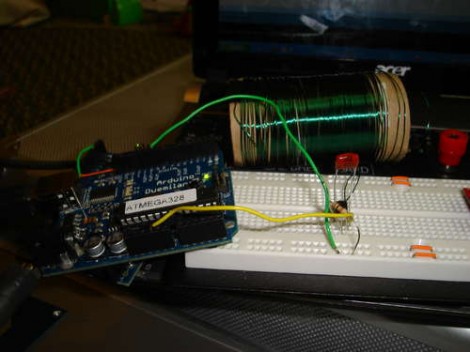
An Arduino, a spent roll of toilet paper, magnet wire, and a few passive components are what’s needed to build this RFID spoofer. It’s quick, dirty, and best of all, simple. However, [SketchSk3tch’s] creation is not an RFID cloner. You must already know the hex code of the tag you want to spoof. That may or may not be as easy as using a separate tag reader.
We’ve seen some very simple RFID tag concepts. What we want is a DIY reader that is easy to build from cheap and readily available components. If you’ve got one, make with the details and tip us off about it.