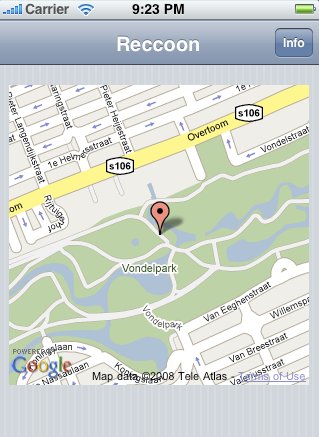
[Dominiek ter Heid] wanted to prototype an application for the iPhone that incorporated GPS. He experimented, and came up with a step-by-step tutorial on how to create a web application that would push GPS information to his iPhone through the use of JavaScript and AJAX. This tutorial will save web hackers who want to play with the iPhone 3G a lot of grief. Using Cocoa Touch, and a CSS/JavaScript pack called IUI, he successfully created a web application that looks native to the iPhone and is able to grab GPS information. The application integrates the GoogleMaps API with the GeoNames database. We look forward to seeing the types of creative applications that this prototype will inspire. What sort of web application would you want to create for the iPhone?
[via digg]