We do hope this project makes you shiver.
“Financial risks” is an audiovisual installation that reacts when you swipe your credit card and prints an odd looking receipt if you type in your pin-code. Even though the website contains few technical details (read none) about the build, we chose to feature the project as we find his intent interesting:
‘Financial Risks’ installation is a project designed to present an ironical viewpoint on encoded wallets, as a data input interface invites to overcome fear of impossibility to control spread of confidential information for the sake of curiosity of interaction with an object of art.
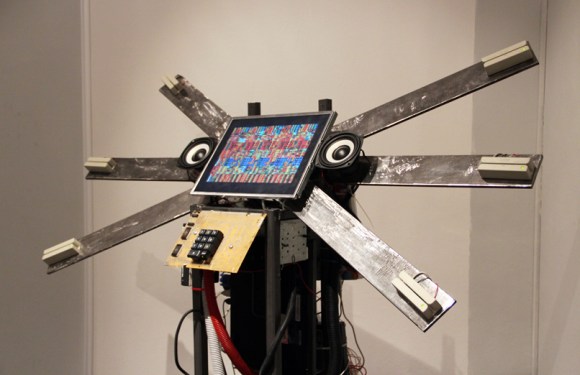
The piece consists of 6 bank card readers, a hardware system of sound and video synthesis, a keyboard for pin code entering, a 2-channel sound system and a cash register printer configured to print images. Up to 6 cards simultaneously may be used for playing.
We do hope that nothing is stored in the platform’s memory… but is the installation monitored?





![A][](http://hackaday.com/wp-content/uploads/2012/04/a.png)