The Nintendo Switch portable gaming system is heavily locked down to prevent hacking, but the Labo add-on looks like it might be a different matter. The Labo is a series of add-on devices made of cardboard that does things like turn the Switch into a musical keyboard that plays a waveform on a card that you slot in. [Hunter Irving] decided to try a bit of reverse engineering on these cards to see if he could 3D print his own. Spoilers: he could.
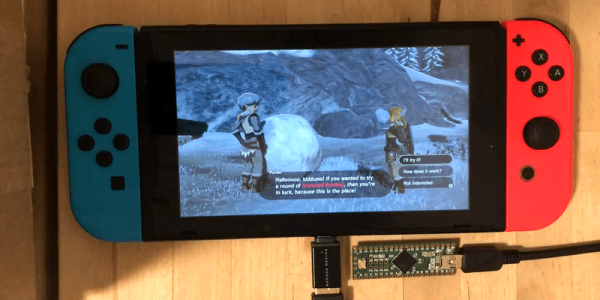
[Hunter] started by taking one of the cards that come with the Labo and looking at the layout. These cards are, like the rest of the Labo, very simple: they are just shaped pieces of card that fit into the back of the keyboard add-on. When you press a button, the Switch camera reads the card to create the waveform. So, the process involved figuring out the required dimensions of the card to create a template. [Hunter] then created simple waveforms (square, sine, sawtooth) in Inkscape, and used this to create a 3D printable waveform card. A quick bit of 3D printing later, he had several cards ready, and these worked without problems. As well as the synthetic waveforms, he tried real ones, such as an organ, taking the waveform shape from the zoomed-in sample and using that to print. This post describes the process nicely and offers downloads of 9 sample cards and a template to create your own.
We suspect that this is only scratching the surface of what can be done with the Switch, Labo, and some ingenuity. Unlike the Switch itself, the Labo seems to be built for hacking, using simple, easy to use components to create surprisingly complex mechanisms that could be adapted for any number of purposes.
We’re sure this isn’t the only Labo hack we’ll be covering over the coming year. Not sure what all the fuss is about? Read our reporting on its arrival.