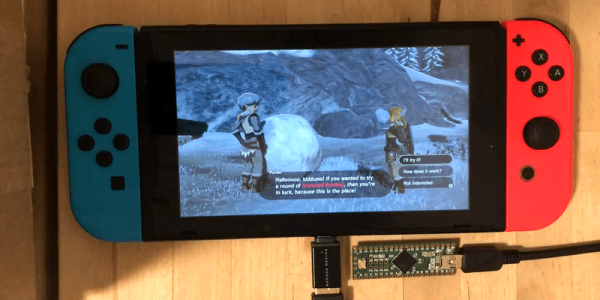
The most recent of the Zelda franchise, Breath of the Wild, is known for its many, many puzzles. One of the more frustrating ones involved bowling with a giant snowball at the top of a hillside. [Bertrand] did not like this, so he cheated the system hacked the Nintendo Switch so that he “genuinely earned” a strike every time he played. He achieved this by writing a script for a Teensy module that got him those sweet rupees.
The Teensy houses an Atmel 90USB1286 microcontroller. When paired with LUFA software, it can emulate numerous controllers including keyboards, joysticks, etc. It also handily has a Mini-B USB connector located on its rear, allowing it to communicate to the Switch with ease. After confirming the hardware was compatible, [Bertrand] looked towards the software side noticing the similarity between what already existed and what he was attempting to accomplish. He happened upon this in a Splatoon 2 fork that allows players to draw posts.
In essence, it takes image files as input and emulates the controls and buttons to draw a 1-bit version of the image automatically. This takes care of syncing the hardware as well as how to simulate the button presses. But instead of reading an image file, it needed to take a custom script as the input. This required starting from scratch. The first logical step — of course — was to create a language similar to Logo, a name that surely brings back memories of the time of big hair and shoulder pads. He only needed a handful of simple commands to control Link:
typedef enum {
UP,
DOWN,
LEFT,
RIGHT,
X,
Y,
A,
B,
L,
R,
THROW,
NOTHING,
TRIGGERS
} Buttons_t;
Continue reading “Teensy Script Plays Nintendo Switch, Strikes Out”