The announcement of Autodesk’s changes to the Fusion 360 personal use license terms this week caused quite a dustup. Our article on the announcement garnered a lot of discussion and not a few heated comments. At the end of the day, though, Autodesk is going to do what it’s going to do, and the Fusion 360 user community is just going to have to figure out how to deal with the changes. One person who decided to do something other than complain is Justin Nesselrotte, who came up with a quick and easy bulk export tool for Fusion 360. This gets to the heart of the issue since the removal of export to STEP, IGES, and SAT files is perhaps the most painful change for our community. Justin’s script automatically opens every design and exports it to the file type of your choice. Since the license changes go into effect on October 1, you’d better get cracking if you want to export your designs.
Over on Twitter, Hackaday superfriend Timon gives us a valuable lesson in “you get what you pay for.” He found that a bunch of his header pin jumper cables weren’t even remotely assembled properly. The conductors of the jumper wire were only loosely inserted into the terminal’s crimp, where apparently no crimping pressure had been applied. The wires were just rattling around inside the crimp, rather than making sold contact. We’ve covered the art and science of crimping before, and it’s pretty safe to say that these jumpers are garbage. So if you’re seeing weird results with a circuit, you might want to take a good, close look at your jumpers. And as always, caveat emptor.
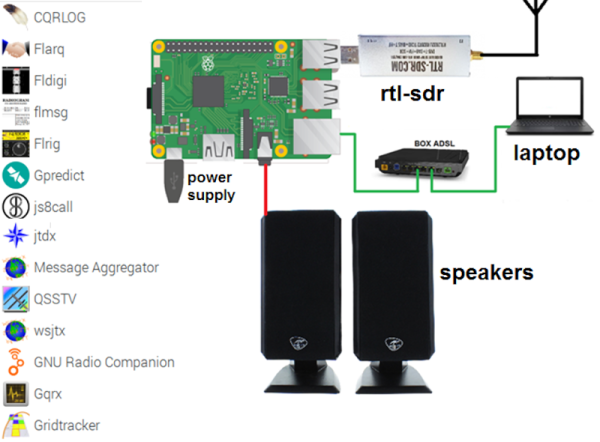
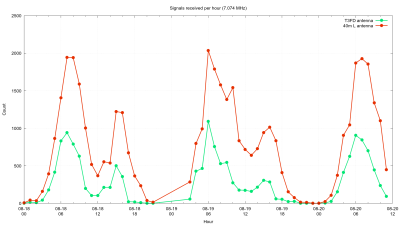
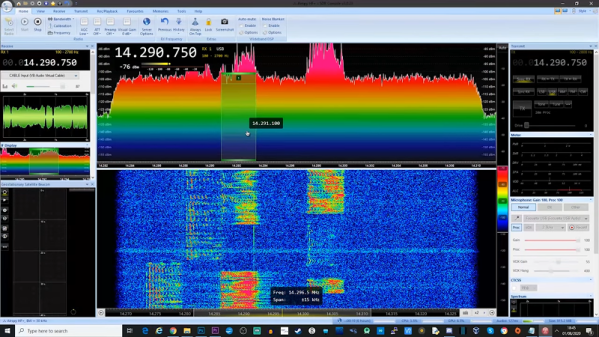
The GNU Radio Conference wrapped up this week, in virtual format as so many other conferences have been this year, and it generated a load of interesting talks. They’ve got each day’s proceedings over on their YouTube channel, so the videos are pretty long; luckily, each day’s stream is indexed on the playbar, so along with the full schedule you can quickly find the talks you’re interested in. One that caught our eye was a talk on the Radio Resilience Competition, a hardware challenge where participants compete head-to-head using SDRs to get signals through in an adversarial environment. It sounds like a fascinating challenge for the RF inclined. More details about registering for the competition can be had on the Radio Resilience website.
You know those recipe sites that give you a few choices on what to make for dinner based on the ingredients you have on hand? We always thought that was a clever idea, and now something like it has come to our world. It’s called DIY Hub, and it aims to guide makers toward projects they can build based on the parts they have on hand. Users create projects on the site, either hosting the project directly on the site or providing a link to projects on another site. Either way, the project’s BOM is cataloged so that users can find something to build based on parts stored in their “Garage”. Granted, most of us suffer from the exact opposite problem of not knowing what to build next, but this could be an interesting tool for stimulating the creative process, especially for teachers and parents. It’s currently in beta, and we’d love to see a few Hackaday.io projects added to the site.
And finally, we got a tip to an oldie but a goodie: How to Build a Castle. No, we don’t expect to see a rash of 13th-century castle builds gracing our pages anytime soon — although we certainly wouldn’t be opposed to the idea. Rather, this is a little something for your binge-watching pleasure. The BBC series, which was actually called Secrets of the Castle, was a five-part 2014 offering that went into great detail on the construction of Guédelon Castle, an experimental archaeology project in France that seeks to build a castle using only the materials and methods available in the 1200s. The series is hosted by historian Ruth Goodman and archaeologists Peter Ginn and Tom Pinfold, and it’s great fun for anyone interested in history and technology.