Huge, fully functional NES game pad replica

Students at Dutch TU Delft university recently built a huge replica of the original NES controller (Google Translation), which is fully functional and can be used to play games on a large display screen they also installed. How big is it, you ask? It’s about 6 meters wide – over 30 times the size of the original NES game pad and requires participants to jump on the buttons to play.
Convert any image to G-code
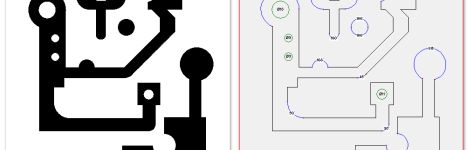
Members of [Forskningsavdelningen], a Swedish hackerspace, are working on software that will allow users to vectorize bitmap images in order to convert them to G-code files for CNC milling. A good portion of the project is complete, but there is still a bit of work to do, so you won’t see it in action for a while. When it’s ready, we’ll be sure to let you know.
Convert your lame Dead Space plasma cutter into a bonafide laser weapon

If you forked out big bucks for the special edition of Dead Space 2, you know how lame the included plasma cutter replica is. Check out this video, that shows you how to convert your LED toy to a dual laser, fire starting, laser pistol. The process is pretty simple, so what are you waiting for?
Synchronized, LED-lit juggling balls

[Jonathan] wrote in to share a project he and some friends have just finished. He’s not sharing a ton of details at the moment, but he has put up a video showing off their wireless LED juggling balls. All we know is that they use bright RGB LEDS, Zigbees for communication, and that they are awesome. We can’t wait to hear more about them!
Water cooled PS3 Laptop

[Pirate] recently unveiled his latest work, a water-cooled Playstation 3 laptop. It looks pretty sharp, and can undoubtedly rival some of Ben Heck’s work, even if it does have an external PSU. Obviously having a separate power component isn’t necessarily ideal, but when you are cramming all of that water cooling goodness into such a small package, something has to give!