Persistence of vision displays are always cool, although we must admit this one looks like it could very well explode at high speeds…
Safety concerns aside, this desk fan based display provides a great starting point for learning about making POV displays. It makes use of an old cellphone battery, an ATmega8, some LEDs, Veroboard, assorted wires and solder and of course, a high-speed desk fan.
[shparvez001] also provides the full code on his blog for the project, making it very easy to replicate. Though we might also suggest you keep it small enough that the original fan cage still fits on top.
From an aesthetic point of view, the display looks fine in the dark — but when the lights are on you might get some odd looks. We can see this project being greatly improved by mounting the LEDs through one of the fan blades, and the control electronics on the back side of the other blades. Maybe throw in some wireless charging for the battery while the fan is off too?
Anyway, stick around after the break to see the display in action. If you want a more permanent fan POV try adding display hardware to a ceiling unit.


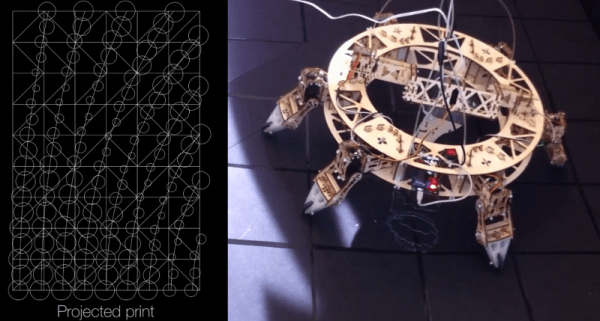

 [Roballoba] decided to
[Roballoba] decided to