[Simon] has been using his home alarm system for over six years now. The system originally came with a small RF remote control, but after years of use and abuse it was finally falling apart. After searching for replacement parts online, he found that his alarm system is the “old” model and remotes are no longer available for purchase. The new system had similar RF remotes, but supposedly they were not compatible. He decided to dig in and fix his remote himself.
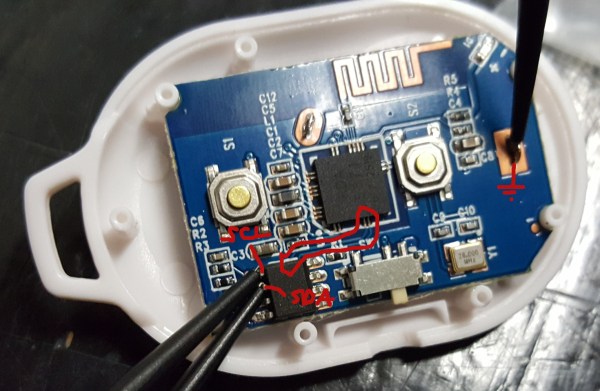
He cracked open the remote’s case and found an 8-pin chip labeled HCS300. This chip handles all of the remote’s functions, including reading the buttons, flashing the LED, and providing encoded output to the 433MHz transmitter. The HCS300 also uses KeeLoq technology to protect the data transmission with a rolling code. [Simon] did some research online and found the thew new alarm system’s remotes also use the same KeeLoq technology. On a hunch, he went ahead and ordered two of the newer model remotes.
He tried pairing them up with his receiver but of course it couldn’t be that simple. After opening up the new remote he found that it also used the HCS300 chip. That was a good sign. The manufacturer states that each remote is programmed with a secret 64-bit manufacturer’s code. This acts as the encryption key, so [Simon] would have to somehow crack the key on his original chip and re-program the new chip with the old key. Or he could take the simpler path and swap chips.
A hot air gun made short work of the de-soldering and soon enough the chips were in place. Unfortunately, the chips have different pinouts, so [Simon] had to cut a few traces and fix them with jumper wire. With the case back together and the buttons in place, he gave it a test. It worked. Who needs to upgrade their entire alarm system when you can just hack the remote?