
[Vivek Ramachandran]’s Cafe Latte attack was one of the last talks we caught at ToorCon. I’ve found quite a few articles about it, but none really get it right. It’s fairly simple and deals with cracking WEP keys from unassociated laptops. First your WEP honeypot tells the client that it has successfully associated. The next thing the client does is broadcast a WEP encrypted ARP packet. By flipping the bits in the ARP packet you can replay the WEP packet and it will appear to the client to be coming from an IP MAC combo of another host on the network. All of the replies will have unique IVs and once you get ~60K you can crack it using PTW. The bit flipping is the same technique used in the fragmentation attack we covered earlier, but Cafe Latte requires generation of far fewer packets. You can read about the Cafe Latte attack on AirTight Networks.
Year: 2007
Tengu Clone
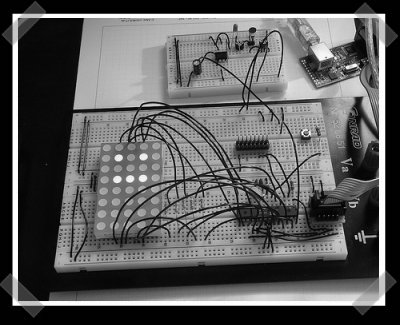
[Alex] sent in his clone of [Crispin Jones]’ tengu. The tengu is essentially a funky visual sound meter that looks like it’s lip syncing. [Alex]’s version is built around an ATMega48 microcontroller, an electric mic with a LM386 audio circuit and the required LED matrix display. There’s an example tengu video here – but I’m not sure what to say about the song in the demo. It’s not dependent on USB – it actually works better with the clean power provided by batteries anyway.
Fiber Optic Flash Ring

Ring lights that surround the lens are generally used for macro photography – they’re not cheap, but they’re one of the few ways to get shadowless photos. This fiber optic flash diffuser is based on the same ideas of this one. Rather than use a few large optic strands, [Joris] is using many, many more to decrease shadows as much as possible. His previous efforts are even more interesting. He built a LED version – with serial connected LEDs and a step up switching power supply to drive them. Then he moved on to cold cathode fluorescent before moving onto the fiber optics.
ToorCon 9: URI Use And Abuse

[Nathan McFeters] and [Rob Carter] gave a presentation on the problems with URI handling. URIs are used to send commands to external applications from a web browser. itms:// for iTunes for example. Any application that registers a URI has the potential to be abused through this route. For their first example they showed a stack overflow in Trillian’s AIM handling. The next demo created a “Critical Update Available” button on Picasa’s interface. When the user clicked it, their photos would be uploaded to the attacker’s server. They even display a “download progress” bar to encourage the user to keep the connection open. You can read about the attack on cocontributor Billy Rios’s blog.
ToorCon 9: CDMA Unlocking And Modification

[Alexander Lash] gave a short overview of what you need to unlock a CDMA phone. He strongly recommended Howard Forums for finding most of the info you need. You’ll probably need BitPim and the Qualcomm PST (product support tools). Using the PST you can flash your new carrier’s firmware and then activate the phone on their network.
Verizon offers two ways to get unlimited EVDO data. $59 for a data plan or $15 for VCast. You’re not supposed to be able to use your VCast phone as an EVDO modem and it sends a different network access identifier (NAI) if you tether the phone. Using the PST you can change the NAI and use the cheaper VCast plan for data access. Here is a forum post detailing the process.
Drive Bay PoE Adapter

Sure, we’ve seen Power over Ethernet before – I even whipped up a simple adapter for my modded wrt54gs. This is a nice clean setup, and it’ll save you from yet another power brick. (I’ve got a power strip dedicated to the things in my tiny home data center.)
ToorCon 9: Real World Fuzzing

We dropped in on [Charlie Miller]’s fuzzing seminar at the end of the day yesterday. Fuzzing become a fairly popular topic in the last year and essentially involves giving a program garbage input, hoping that it will break. If it can’t handle the fake data and fails in a non-graceful fashion, you could have found a potentially exploitable bug. Fuzzing is a fairly simple idea, but as Charlie points out, without some thinking while you’re doing it it’s unlikely to be very productive.










