OK, let’s start this one by saying that it’s useful to know how to break security measures in order to understand how to better defend yourself, and that you shouldn’t break into any network you don’t have access to. That being said, if you want to learn about security and the weaknesses within the WPA standard, there’s no better way to do it than with a tool that mimics the behavior of a Tamagotchi.
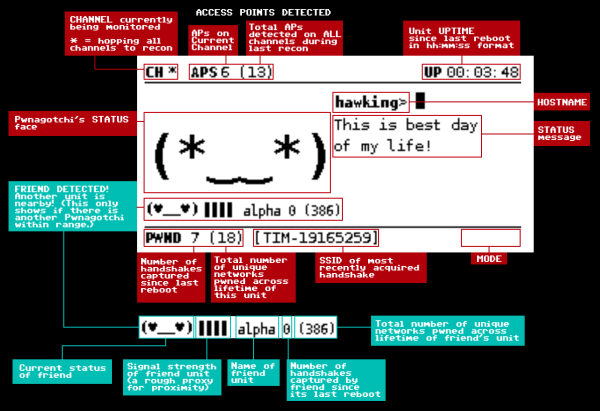
Called the pwnagotchi, this package of artificial intelligence looks for information in local WiFi packets that can be used to crack WPA encryption. It’s able to modify itself in order to maximize the amount of useful information it’s able to obtain from whatever environment you happen to place it in. As an interesting design choice, the pwnagotchi behaves like an old Tamagotchi pet would, acting happy when it gets the inputs it needs.
This project is beyond a novelty though and goes deep in the weeds of network security. If you’re at all interested in the ways in which your own networks might be at risk, this might be a tool you can use to learn a little more about the ways of encryption, general security, and AI to boot. Of course, if you’re new to the network security world, make sure the networks you’re using are secured at least a little bit first.
Thanks to [Itay] for the tip!