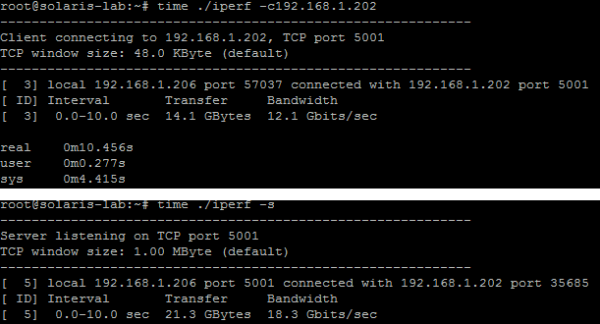
Today we heard from [Richard James Howe] about his new CPU. This new 16-bit CPU is implemented in VHDL for an FPGA.
The really cool thing about this CPU is that it eschews the typical program counter (PC) and replaces it with a linear-feedback shift register (LFSR). Apparently an LFSR can be implemented in hardware with fewer transistors than are required by an adder.
Usually the program counter in your CPU increments by one, each time indicating the location of the next instruction to fetch and execute. When you replace your program counter with an LFSR it still does the same thing, indicating the next instruction to fetch and execute, but now those instructions are scattered pseudo-randomly throughout your address space!