Over the last several months, [Aaron Christophel] has been working on creating a custom firmware for cheap fitness trackers. His current target is the “D6 Tracker” from a company called MPOW, which can be had for as little as $7 USD. The ultimate goal is to make it so anyone will be able to write their own custom firmware for this gadget using the Arduino IDE, and with the release of his new Android application that allows wirelessly flashing the device’s firmware, it seems like he’s very close to realizing that dream.
Previously, [Aaron] had to crack open the trackers and physically connect a programmer to update the firmware on the NRF52832-based devices. That might not be a big deal for the accomplished hardware hacker, but it’s a bit of a hard sell for somebody who just wants to see their own Arduino code running on it. But with this new tool, he’s made it so you can easily switch back and forth between custom and original firmware on the D6 without even having to take it off your wrist.
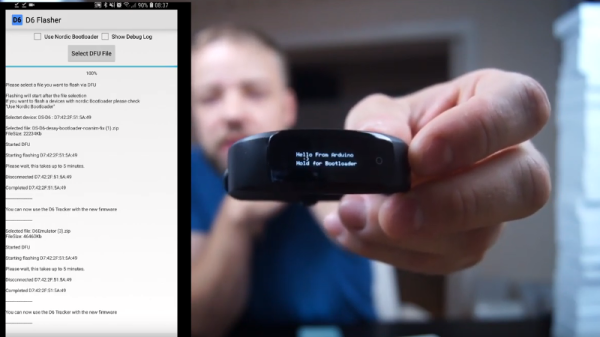
After the break, you can see the video that [Aaron] has put together which talks about the process of flashing a new firmware image. It’s all very straightforward: you simply pick the device from the list of detected BLE devices, the application puts the tracker into bootloader mode, and then you select the DFU file you want to flash.
There are a couple of ready-made firmwares you can put on the D6 right now, but where’s the fun in that? [Aaron] has put together a customized version of the Arduino IDE that provides everything you need to start writing and flashing your own firmware. If you’ve ever dreamed about creating a wearable device that works exactly the way you want, it’s hard to imagine a cheaper or easier way to get in on the action.
When we last heard from [Aaron] earlier this year, he was working on the IWOWN I6HRC tracker. But it looks like the availability of those devices has since dried up. So if you’re going to try your hand at hacking the MPOW D6, it might be wise to buy a few now while they’re still cheap and easy to find.
Continue reading “OTA Flash Tool Makes Fitness Tracker Hacking More Accessible”