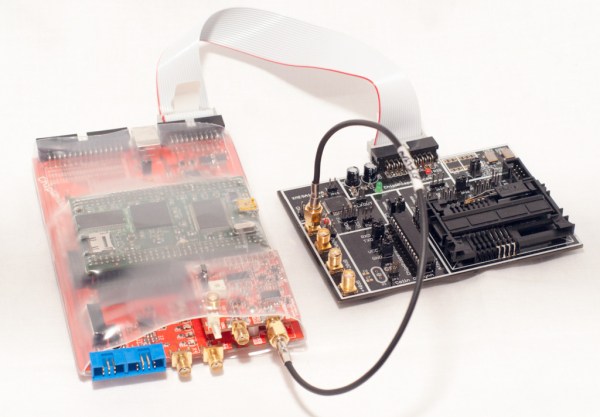
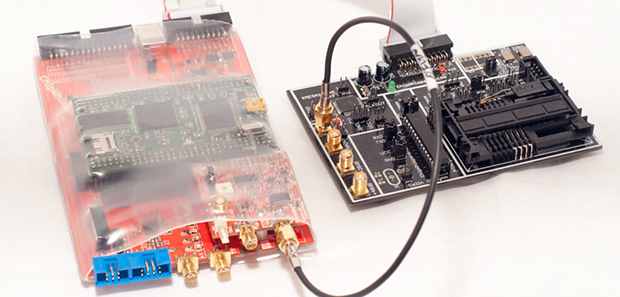
The ChipWhisperer has been a breakthrough in hobbyist use of power analysis and glitching attacks on embedded hardware. If you own one, you surely have seen the IDC and SMA sockets on it – usable for connecting custom breakouts housing a chip you’re currently probing. Today, [MAVProxyUser] brings us a ChipWhisperer adapter for STM32F446ZEJx, which comes in a UFBGA144 package – and the adapter has quite a backstory to it.
In retro gaming world, a crowdfunding campaign for a game called PAPRIUM has seen a huge success getting funded in 2017. However, the campaign has grossly underdelivered throughout the last five years, and out of those rare cartridges delivered to backers, quite a few have faulty hardware. Getting replacements isn’t realistic at this point, so the repair attempts and game preservation efforts have been ongoing. Trouble is – there are protection mechanisms against dumping the cartridges, and one of the protection mechanisms is the built-in flash read protection of the aforementioned STM32 found on the cartridge. This board adapts the chip to a ChipWhisperer interface for protection bypass exploration, and has quite a few configuration jumpers anyone facing a similar chip is able to use – Eagle files are out there as well, in case your chip needs a slightly different approach.
With reverse-engineering underway, are we likely to see this cartridge’s defenses fall? Our assessment is ‘yes’ – it’s not like there’s a shortage of mechanisms for bypassing security ; from modchips to EMP attacks to blasting the die with a laser, hardware-reliant security is, still, quite bypassable. All in all, despite the drama around the project, this is one more reference design for the ChipWhisperer, and a fun journey to look forward to.