Over the past two decades, e-paper has evolved from an exotic and expensive display technology to something cheap enough to be used for supermarket price tags. While such electronic shelf labels are now easy to find, actually re-using them is often tricky due to a lack of documentation. Luckily, [Aaron Christophel] has managed to reverse engineer many types of shelf labels, and he’s demonstrated the results by turning one into an ultra-low-power clock called Triink. It’s based on a 128×296 pixel e-ink display paired with an nRF52832 BlueTooth Low-Energy SoC and uses just 65 micro-amperes on average: low enough to keep it running for more than a year on a single battery charge.
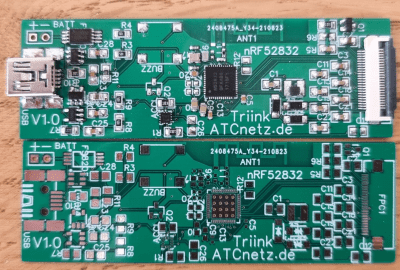
The clock is housed in an enclosure that’s simple but effective: a 3D-printed triangular prism with a slot for the screen and space for the 18650 lithium battery. One side can be opened to access the internal components, although that’s really only needed to charge the battery. You can see how cleverly everything snaps together in the video embedded below. Continue reading “Low Power Challenge: E-Paper Shelf Label Becomes Ultra-Frugal Clock”