This week, Editor-in-Chief Elliot Williams and Kristina Panos met up to discuss the best hacks of the previous week. It’s CES time once again in Las Vegas, and you know what that means — some wacky technologies like this AI pet door that rejects dead mice.
Then it’s on to What’s That Sound, which Kristina managed to nail for once. Can you get it? Can you figure it out? Can you guess what’s making that sound this week? If you can, and your number comes up, you get a special Hackaday Podcast t-shirt.
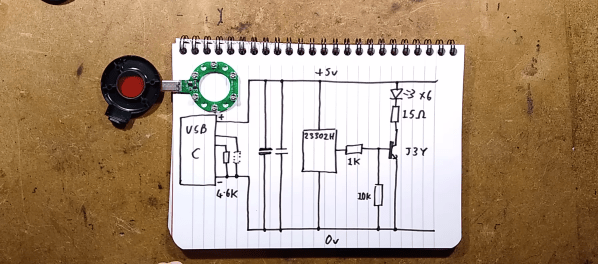
But then it’s on to the hacks, beginning with a new keyboard from [Joe Scotto] and an exploration of all you can do with an LED strip, like 1D fireworks and roller coasters without any moving parts. From there, we marvel at the ability of sound waves to extinguish flames, and the tech behind life as a quadriplegic. Finally, we examine not one, but two of Jenny List’s finely-crafted rants, one about web browsers, and the other about the responsible use of new technology.
Check out the links below if you want to follow along, and as always, tell us what you think about this episode in the comments!