We’re used to our domestic appliances being completely automated in 2020, but not so long ago they were much simpler affairs. Not everything required a human to run it though, an unexpected piece of electromechanical automation could be found in British bedrooms. This is the story of the Goblin Teasmade, an alarm clock with a little bit extra.
Hackaday Columns4664 Articles
This excellent content from the Hackaday writing crew highlights recurring topics and popular series like Linux-Fu, 3D-Printering, Hackaday Links, This Week in Security, Inputs of Interest, Profiles in Science, Retrotechtacular, Ask Hackaday, Teardowns, Reviews, and many more.
DDR-5? DDR-4, We Hardly Knew Ye
This month’s CES saw the introduction of max speed DDR5 memory from SK Hynix. Micron and other vendors are also reportedly sampling similar devices. You can’t get them through normal channels yet, but since you also can’t get motherboards that take them, that’s not a big problem. We hear Intel’s Xeon Sapphire Rapids will be among the first boards to take advantage of the new technology. But that begs the question: what is it?
SDRAM Basics
Broadly speaking, there are two primary contenders for a system that needs RAM memory: static and dynamic. There are newer technologies like FeRAM and MRAM, but the classic choice is between static and dynamic. Static RAM is really just a bunch of flip flops, one for each bit. That’s easy because you set it and forget it. Then later you read it. It can also be very fast. The problem is a flip flop usually takes at least four transistors, and often as many as six, so there’s only so many of them you can pack into a certain area. Power consumption is often high, too, although modern devices can do pretty well.
RF Modulation: Crash Course For Hackers
When you’re looking to add some wireless functionality to a project, there are no shortage of options. You really don’t need to know much of the technical details to make use of the more well-documented modules, especially if you just need to get something working quickly. On the other hand, maybe you’ve gotten to the point where you want to know how these things actually work, or maybe you’re curious about that cheap RF module on AliExpress. Especially in the frequency bands below 1 GHz, you might find yourself interfacing with a module at really low level, where you might be tuning modulation parameters. The following overview should give you enough of an understanding about the basics of RF modulation to select the appropriate hardware for your next project.
Three of the most common digital modulation schemes you’ll see in specifications are Frequency Shift Keying (FSK), Amplitude Shift Keying (ASK), and LoRa (Long Range). To wrap my mechanically inclined brain around some concepts, I found that thinking of RF modulation in terms of pitches produced by a musical instrument made it more intuitive.
And lots of pretty graphs don’t hurt either. Signals from two different RF dev boards were captured and turned into waterfall and FFT plots using a $20 RTL-SDR dongle. Although not needed for wireless experimentation, the RTL-SDR is an extremely handy debugging tool, even to just check if a module is actually transmitting. Continue reading “RF Modulation: Crash Course For Hackers”
Open-Source Medical Devices Hack Chat
Join us on Wednesday, January 29 at noon Pacific for the Open-Source Medical Devices Hack Chat with Tarek Loubani!
In most of the developed world, when people go to see a doctor, they’re used to seeing the latest instruments and devices used. Most exam rooms have fancy blood pressure cuffs, trays of shiny stainless steel instruments, and a comfortable exam table covered by a fresh piece of crisp, white paper. Exams and procedures are conducted in clean, quiet places, with results recorded on a dedicated PC or tablet.
Such genteel medical experiences are far from universal, though. Many clinics around the world are located in whatever building is available, if they’re indoors at all. Supplies may be in chronically short supply, and to the extent that the practitioners have the instruments they need to care for patients, they’ll likely be older, lower-quality versions.
Tarek Loubani is well-versed in the practice of medicine under conditions like these, as well as far worse situations. As an emergency physician and researcher in Canada, he’s accustomed to well-appointed facilities and ample supplies. But he’s also involved in humanitarian relief, taking his medical skills and limited supplies to places like Gaza. He has seen first-hand how lack of the correct tools can lead to poor outcomes for patients, and chose to fight back by designing a range of medical devices and instruments that can be 3D-printed. His Glia Project has free plans for a high-quality stethoscope that can be built for a couple of dollars, otoscopes and pulse oximeters, and a range of surgical tooling to make the practice of medicine under austere conditions a little easier. Continue reading “Open-Source Medical Devices Hack Chat”
CRISPR Could Fry All Cancer Using Newly Found T-Cell
One of the human body’s greatest features is its natural antivirus protection. If your immune system is working normally, it produces legions of T-cells that go around looking for abnormalities like cancer cells just to gang up and destroy them. They do this by grabbing on to little protein fragments called antigens that live on the surface of the bad cells and tattle on their whereabouts to the immune system. Once the T-cells have a stranglehold on these antigens, they can release toxins that destroy the bad cell, while minimizing collateral damage to healthy cells.
This rather neat human trick doesn’t always work, however. Cancer cells sometimes mask themselves as healthy cells, or they otherwise thwart T-cell attacks by growing so many antigens on their surface that the T-cells have no place to grab onto.
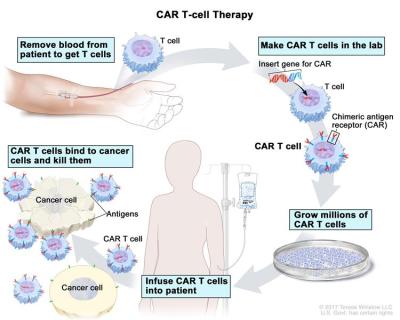
Medical science has come up with a fairly new method of outfoxing these crafty cancer cells called CAR T-cell therapy. Basically, they withdraw blood from the patient, extract the T-cells, and replace the blood. The T-cells are sent off to a CRISPR lab, where they get injected with a modified, inactive virus that introduces a new gene which causes the T-cells to sprout a little hook on their surface.
This hook, which they’ve dubbed the chimeric antigen receptor (CAR), allows the T-cell to chemically see through the cancer cells’ various disguises and attack them. The lab multiplies these super soldiers and sends them back to the treatment facility, where they are injected into the patient’s front lines.
Continue reading “CRISPR Could Fry All Cancer Using Newly Found T-Cell”
Hackaday Belgrade Early Bird Tickets On Sale Right Now
Tickets for Hackaday Belgrade 2020 just went on sale. If you’re quick you can grab an Early Bird ticket at half the price of general admission!
Hackaday’s premiere European hardware conference returns for the third time on May 9th, 2020, bringing together talks, workshops, hardware hacking, food and drink, entertainment, and of course the best gathering of hardware geeks you’ll find anywhere. It’s awesome, because you’re awesome — and I do mean you. Whether you’re submitting a talk proposal or just grabbing a ticket to make this the first conference you’ve ever been to, we can’t do it without you.
Hackaday’s Home in Serbia
We’ll be at Dom Omladine again this year. The venue has feels like a home for Hackaday with a large space for talks, a workshop area, and a huge open area for lobby-con where you’ll find Belgrade’s finest baristas, a great spread of food, and a beer tap to keep the day rolling. Bring along your hardware projects to hack alongside the conference’s custom hardware badge designed by Voja Antonic as we open up the bar and get the live IDM sets started.
It’s still early in our planning (these are Early Bird tickets after all) but it’s very likely we’ll have a meetup the night before the conference. Friends old and new often get together on Sunday to keep the fun going. On Saturday, doors for the conference will open around 9 am and the fun will continue well beyond the 2 am “official” end. We recommend you make travel plans to include the full weekend.

Don’t just ask for Friday off of work, bring your friends and co-workers along with you. If you’re most comfortable digging through datasheets while a hot soldering iron idles on your bench and a 3D-printer whirs away in the corner, Hackaday Belgrade is calling you. I encourage those who were at the first two events in 2016 and 2018 to share their stories below.
Don’t miss this one, it only comes around in even-numbered years and tickets will sell out.
Hackaday Belgrade 2020 Posters by Aleksandar Bradic (click for full size download link):
Hackaday Links: January 26, 2019
The news this week was dominated by the novel coronavirus outbreak centered in Wuhan, China. Despite draconian quarantines and international travel restrictions, the infection has spread far beyond China, at least in small numbers. A few cases have been reported in the United States, but the first case reported here caught our eye for the technology being used to treat it. CNN and others tell us that the traveler from Wuhan is being treated by a robot. While it sounds futuristic, the reality is a little less sci-fi than it seems. The device being used is an InTouch Vici, a telemedicine platform that in no way qualifies as a robot. The device is basically a standard telepresence platform that has to be wheeled into the patient suite so that providers can interact with the patient remotely. True, it protects whoever is using it from exposure, but someone still has to gown up and get in with the patient. We suppose it’s a step in the right direction, but we wish the popular press would stop slapping a “robot” label on things they don’t understand.
Also in health news, did you know you’re probably not as hot as you think you are? While a glance in the mirror would probably suffice to convince most of us of that fact, there’s now research that shows human body temperature isn’t what it used to be. Using medical records from the Civil War-era to the 1930s and comparing them to readings taken in the 1970s and another group between 2007 and 2017, a team at Stanford concluded that normal human body temperature in the USA has been slowly decreasing over time. They proposed several explanations as to why the old 98.6F (37C) value is more like 97.5F (36.4C) these days, the most interesting being that general overall inflammation has decreased as sanitation and food and water purity have increased, leading the body to turn down its thermostat, so to speak. Sadly, though, if the trend holds up, our body temperature will reach absolute zero in only 111,000 years.
Wine, the not-an-emulator that lets you run Windows programs on POSIX-compliant operating systems, announced stable release 5.0 this week. A year in the making, the new version’s big features are multi-monitor support with dynamic configuration changes and support for the Vulkan spec up to version 1.1.126.
Any color that you want, as long as it’s amorphous silicon. Sono Motors, the German start-up, has blown past its goal of raising 50 million euros in 50 days to crowdfund production of its Sion solar-electric car. The car is planned to have a 255 km range on a full charge, with 34 km of that coming from the solar cells that adorn almost every bit of the exterior on the vehicle. Living where the sun doesn’t shine for a third of the year, we’re not sure how well this will pay off, but it certainly seems smarter than covering roads with solar cells.
And finally, here’s a trip down memory lane for anyone who suffered through some of the cringe-worthy depictions of technology that Hollywood came up with during the 70s, 80s, and 90s. Looking back through the clips shown in “copy complete” reminds us just how many movies started getting into the tech scene. It wasn’t just the sci-fi and techno-thrillers that subjected us to closeups of scrolling random characters and a terminal that beeped every time something changed on the screen. Even straight dramas like Presumed Innocent and rom-coms like You’ve Got Mail and whatever the hell genre Ghost was got in on the act. To be fair, some depictions were pretty decent, especially given the realities of audience familiarity with tech before it became pervasive. And in any case, it was fun to just watch and remember when movies were a lot more watchable than they are today.