Radio direction finding is one of those things that most Hackaday readers are likely to be familiar with at least on a conceptual level, but probably without much first-hand experience. After all it’s not everyday that you need to track down a rogue signal, let alone have access to the infrastructure necessary to triangulate its position. But thanks to the wonders of the Internet, at least the latter excuse is now a bit less valid.
The RTL-SDR Blog has run a very interesting article wherein they describe how the global network of Internet-connected KiwiSDR radios can be used for worldwide radio direction finding. If you’ve got a target in mind, and the time to fiddle around with the web-based SDR user interface, you now have access to the kind of technology that’s usually reserved for world superpowers. Indeed, the blog post claims this is the first time such capability has been put in the hands of the unwashed masses. Let’s try not to mess this up.
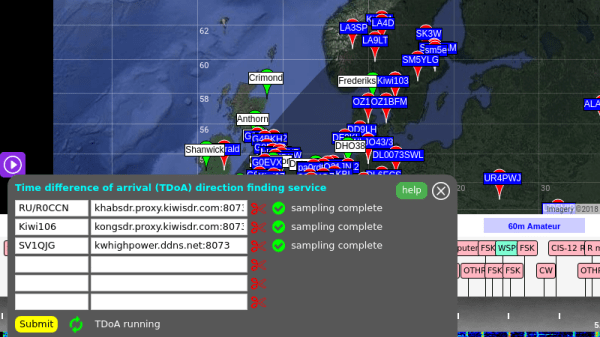
To start with, you should have a rough idea of where the signal is originating from. It doesn’t have to be exact, but you want to at least know which country to look in. Then you pick one of the nearby public KiwiSDR stations and tune the frequency you’re after. Repeat the process for a few more stations. In theory the more stations you have the better, but technically three should be enough to get you pretty close.
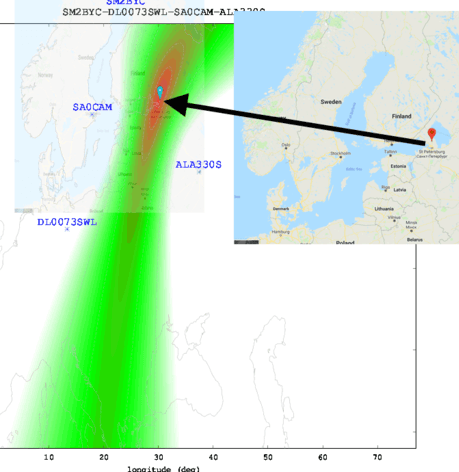
With your receiving stations selected, the system will then start Time Difference of Arrival (TDoA) sampling. This technique compares the time the signal arrives at each station in relation to the KiwiSDR’s GPS synchronized clock. With enough of this data from multiple stations, it can estimate the origin of the signal based on how long it takes to reach different parts of the globe.
It’s not perfect, but it’s pretty impressive for a community run project. The blog post goes on to give examples of both known and unknown signals they were able to triangulate with surprising accuracy: from the US Navy’s VLF submarine transmitter in Seattle, Washington to the mysterious “Buzzer” number station hidden somewhere in Russia.
We’ve covered small-scale triangulation using Wi-Fi, and even a project that aimed to use drones to home in on rescue beacons, but the scale of the KiwiSDR TDoA system is really on a whole new level. Use it wisely.

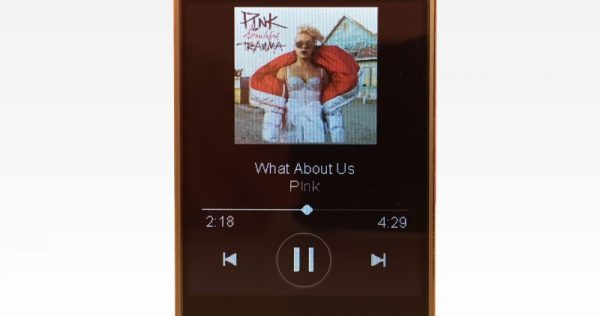
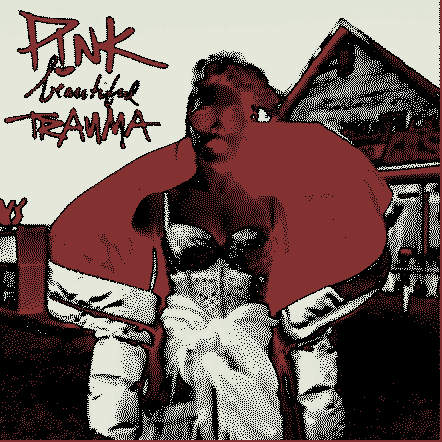
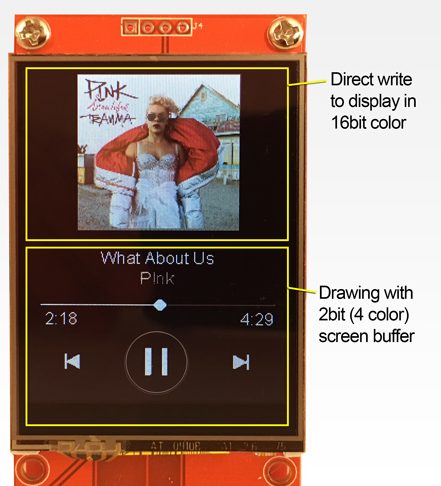 The second problem was smooth drawing. By the ESP’s standards the album art for a given track at full color depth is pretty storage-large, meaning slow transfers to the display and large memory requirements. [Dani] used a few tricks here. The first was to try 2 bit color depth which turned out atrociously (see image above). Eventually the solution became to decompress and draw the album art directly to the screen (instead of a frame buffer) only when the track changed, then redraw the transport controls quickly with 2 bit color. The final problem was that network transfers were also slow, requiring manual
The second problem was smooth drawing. By the ESP’s standards the album art for a given track at full color depth is pretty storage-large, meaning slow transfers to the display and large memory requirements. [Dani] used a few tricks here. The first was to try 2 bit color depth which turned out atrociously (see image above). Eventually the solution became to decompress and draw the album art directly to the screen (instead of a frame buffer) only when the track changed, then redraw the transport controls quickly with 2 bit color. The final problem was that network transfers were also slow, requiring manual 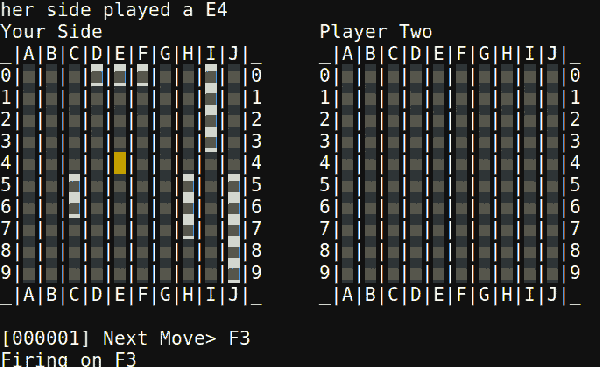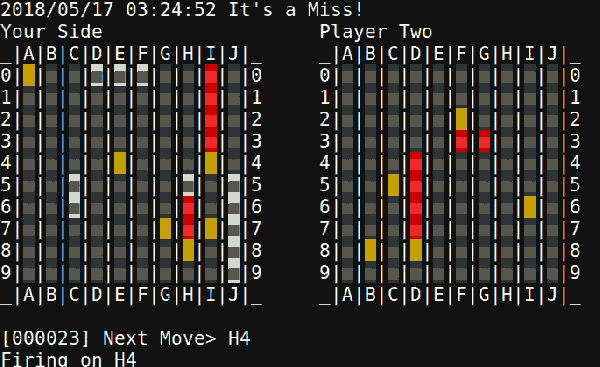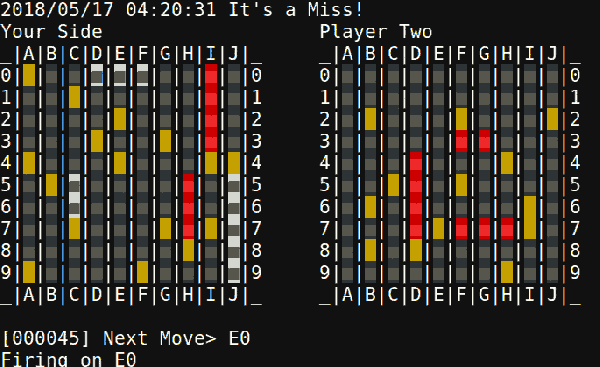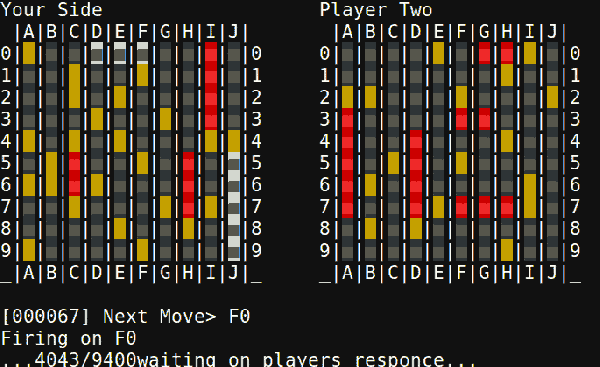

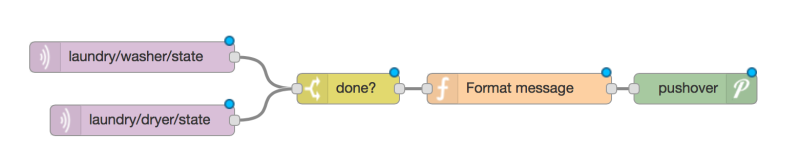
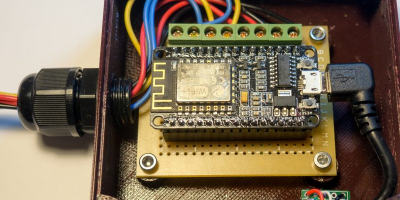 How do you sense when the machine — either a washer or a dryer — is done? [Andrew] thought about sensing current but didn’t want to mess with house current. His machines don’t have LED indicators, so using a light sensor wasn’t going to work either. However, an accelerometer can detect vibrations in the machine and most washers and dryers vibrate plenty while they are running.
How do you sense when the machine — either a washer or a dryer — is done? [Andrew] thought about sensing current but didn’t want to mess with house current. His machines don’t have LED indicators, so using a light sensor wasn’t going to work either. However, an accelerometer can detect vibrations in the machine and most washers and dryers vibrate plenty while they are running.