It’s been nearly four years since the Arecibo Telescope collapsed, an event the world got to witness in unprecedented detail thanks to strategically positioned drones. They captured breathtaking video of one of the support cables pulling from its socket as well as the spectacularly destructive results of 900 tons of scientific instruments crashing into the 300-meter primary reflector. But exactly why did those cable sockets fail?
A new report aims to answer that question, and in the process raises some interesting questions of its own. The proximate causes of the collapse have been known for a while, including the most obvious and visible one, the failure of the zinc “spelter sockets” that were cast around the splayed ends of the wire ropes to hold them in place. The new report agrees with this conclusion, at least in part, implicating “zinc creep,” or the tendency for zinc to deform over time under load. Where it appears to differ, though, is with the quality of workmanship on the sockets, finding no issues with the way the individual wires in the failed support cable were manually splayed within the socket before the molten zinc was poured. The report also points out that the collapse probably started when Hurricane Maria swept over Puerto Rico 39 months before the collapse, after which zinc creep in the sockets seemed to accelerate.
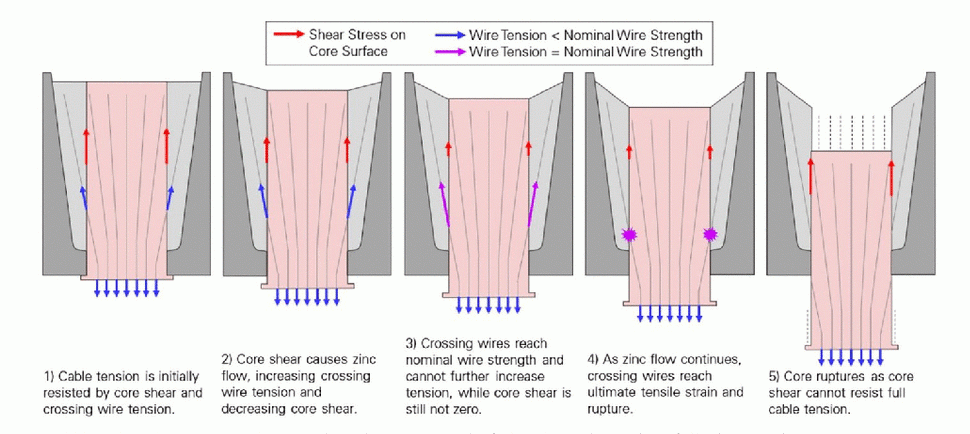
But why did the sockets fail? As the report points out, spelter sockets are commonly used to anchor cables that support heavy loads under conditions similar to the tropical climate at Arecibo. After ruling out every other cause, the committee was left with the conclusion that Arecibo itself may have been to blame for the accelerated zinc creep, thanks to electrical currents induced in the cables and sockets when the telescope’s powerful transmitters were used. They call this “long-term, low-current electroplasticity.” Electroplastic effects have been observed since the 1950s, and while far from certain that’s what happened here, the thought is that skin-effect currents induced in the support cables flowed to ground through the zinc sockets, increasing the plasticity of the metal and accelerating the zinc creep that ultimately led to collapse.
Case closed? Hardly. The electroplasticity mechanism for the Arecibo collapse offered by this report is almost a “diagnosis of exclusion” situation. It makes sense, though; since no other spelter sockets have ever failed this way in a century of use, there’s a good chance that the root cause was specific to Arecibo, and since it was once the world’s most powerful radio transmitter, it seems like a red flag that bears further investigation.


















