Back in 2013, the NSA ANT Catalog was leaked. This document contained a list of devices that are available to the NSA to carry out surveillance.
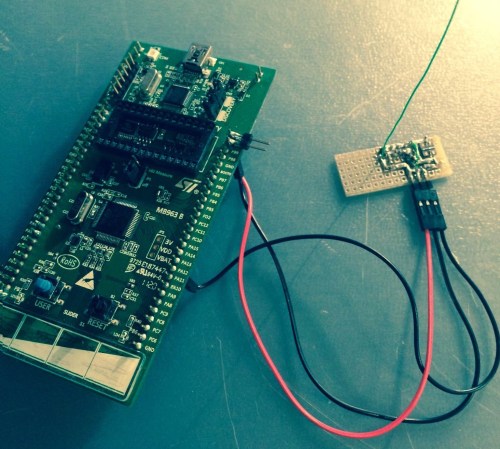
[Michael Ossmann] took a look at this, and realized that a lot of their tools were similar to devices the open source hardware community had built. Based on that, he gave a talk on The NSA Playset at Toorcamp 2014. This covered how one might implement these devices using open hardware.
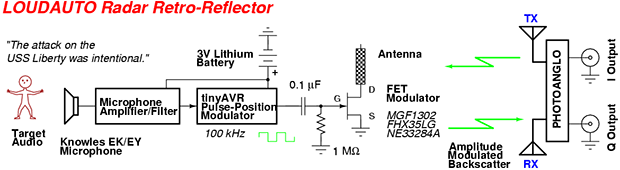
The above image is a parody of an ANT Catalog page, which shows [Michael]’s HackRF, an open source software defined radio. In the talk, [Michael] and [Dean Pierce] go over the ANT Catalog devices one by one, discussing the hardware that would be needed to build your own.
Some of these tools already have open source counterparts. The NIGHTSTAND WiFi exploitation tools is essentially a WiFi Pineapple. SPARROW II is more or less a device running Kismet attached to a drone, which we’ve seen before.
A video of the Toorcamp talk is available on [Michael]’s blog. There will also be a variety of talks on this subject at DEFCON next week, which we’re looking forward to. For further reading, Wikipedia has a great summary of the ANT Catalog.