[Tod’s] daughter has a habit of forgetting to take a house key along with her, so he was looking for a way to make accessing the house easier in a pinch. He had tried wireless garage door keypads in the past, but their performance was so-so at best. After scouring the market for commercial solutions and checking out the work of other hackers, he decided that he needed to craft a custom solution of his own.
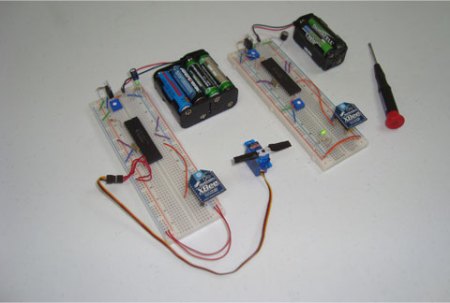
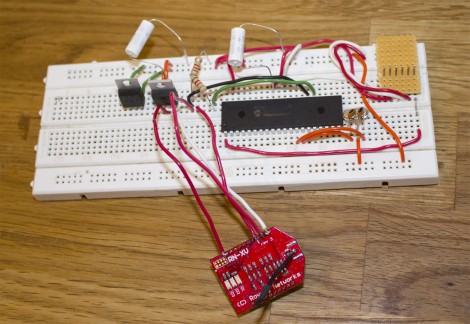
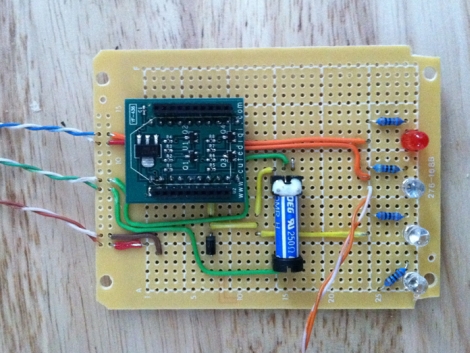
He started shopping around for wireless-enabled microcontrollers and settled on a Roving Networks RN-XV module, which is designed as a drop-in replacement for an XBee. Paired with a 5v to 3.3v power adapter, the RN-XV is nearly all he needed to interface his iPhone with his garage door opener.
The microcontroller has enough GPIO pins to control the garage door, while also monitoring the door’s status using a simple magnet/reed switch combo. A web server in [Tod’s] house takes input from any phone connected to his wireless LAN and relays the open/close commands to the opener. The opener in turn returns status messages to him via the web interface.
We really like the system’s simple design, and as long as [Tod] has turned WPS off at home, he really shouldn’t have to worry too much about unauthorized entry.