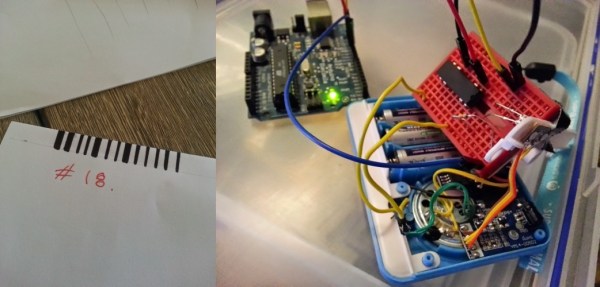
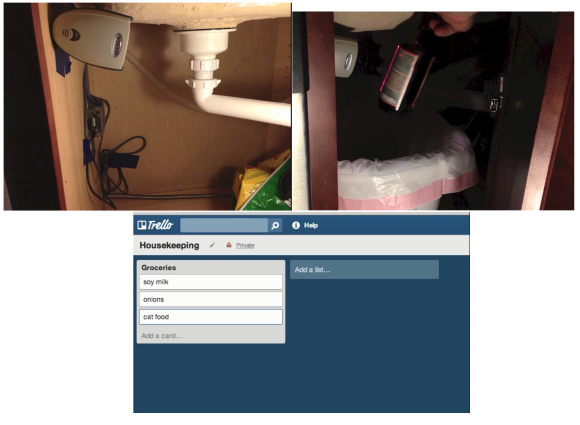
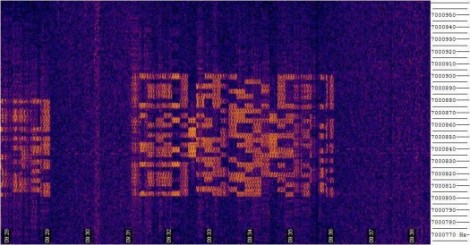
Beep. You hear it every time you buy a product in a retail store. The checkout person slides your purchase over a scanner embedded in their checkout stand, or shoots it with a handheld scanner. The familiar series of bars and spaces on the label is digitized, decoded to digits, and then used as a query to a database of every product that particular store sells. It happens so often that we take it for granted. Modern barcodes have been around for 41 years now. The first product purchased with a barcode was a 10 pack of Juicy Fruit gum, scanned on June 26, 1974 at Marsh supermarket in Troy, Ohio. The code scanned that day was UPC-A, the same barcode used today on just about every retail product you can buy.
The history of the barcode is not as cut and dry as one would think. More than one group has been credited with inventing the technology. How does one encode data on a machine, store it on a physical media, then read it at some later date? Punch cards and paper tape have been doing that for centuries. The problem was storing that data without cutting holes in the carrier. The overall issue was common enough that efforts were launched in several different industries.