It’s been a busy week in space news, and very little of it was good. We’ll start with the one winner of the week, Firefly’s Blue Ghost Mission 1, which landed successfully on the Moon’s surface on March 2. The lander is part of NASA’s Commercial Lunar Payload Services program and carries ten scientific payloads, including a GPS/GNSS receiver that successfully tracked signals from Earth-orbiting satellites. All of the scientific payloads have completed their missions, which is good because the lander isn’t designed to withstand the long, cold lunar night only a few days away. The landing makes Firefly the first commercial outfit to successfully soft-land something on the Moon, and being the first at anything is always a big deal.
bricking7 Articles
Hackaday Links: August 11, 2024
“Please say it wasn’t a regex, please say it wasn’t a regex; aww, crap, it was a regex!” That seems to be the conclusion now that Crowdstrike has released a full root-cause analysis of its now-infamous Windows outage that took down 8 million machines with knock-on effects that reverberated through everything from healthcare to airlines. We’ve got to be honest and say that the twelve-page RCA was a little hard to get through, stuffed as it was with enough obfuscatory jargon to turn off even jargon lovers such as us. The gist, though, is that there was a “lack of a specific test for non-wildcard matching criteria,” which pretty much means someone screwed up a regular expression. Outside observers in the developer community have latched onto something more dire, though, as it appears the change that brought down so many machines was never tested on a single machine. That’s a little — OK, a lot — hard to believe, but it seems to be what Crowdstrike is saying. So go ahead and blame the regex, but it sure seems like there were deeper, darker forces at work here.
Hackaday Links: December 18, 2022
By now everyone has probably seen the devastation wrought by the structural failure of what was once the world’s largest free-standing cylindrical aquarium. The scale of the tank, which until about 5:50 AM Berlin time on Friday graced the lobby of the Raddison Blu hotel, was amazing — 16 meters tall, 12 meters in diameter, holding a million liters of saltwater and some 1,500 tropical fish. The tank sat atop a bar in the hotel lobby and was so big that it even had an elevator passing up through the middle of it.
But for some reason, the tank failed catastrophically, emptying its contents into the hotel lobby and spilling the hapless fish out into the freezing streets of Berlin. No humans were killed by the flood, which is miraculous when you consider the forces that were unleashed here. Given the level of destruction, the displaced hotel guests, and the fact that a €13 million structure just up and failed, we’re pretty sure there will be a thorough analysis of the incident. We’re pretty interested in why structures fail, so we’ll be looking forward to finding out the story here.
Slingbox Getting Bricked – You Have Less Than 24 Hours
The Slingbox devices used to let you catch up with the programming on your TV when you weren’t near it, using your Internet-connected mobile device. As cable TV became less popular, their business model faded away, and in 2020, they scheduled a service shutdown for November 9th, 2022. If you own a Slingbox, it’s getting bricked tomorrow – for those reading this in EU, that’ll be today, even. Do you have a Slingbox? You might still be able to repurpose it, let’s say, for local media streaming – but only if you waste no time.
[Gerry Dubois] has been developing the “Slinger” software for the past few months, a small app you run locally that proxies commands and video for your Slingbox, thanks to reverse-engineering communications with Slingbox servers. However, it needs a “hardware password” alphanumeric string, that you need to get from the Slingbox service web interface – which is to be promptly shut down. If you think you might have a use for what’s essentially a network-connected analog/digital video capture card with decent hardware, the GitHub repo has a lively discussion tab for any questions you might have.
One one hand, Slingbox shouldn’t be bricking the devices in a way that requires you act fast – perhaps, releasing a final update that makes the device hacker-friendly, like O2 did with their Joggler appliance back in the day, publishing the hardware documentation, or at least setting up a service up that lets anyone retrieve their hardware password indefinitely. On the other hand, at least they gave us two years’ notice, something less than usual – the amount of time between bricking and an announcement can even be a negative number. For those of us stuck with no operational device, a hardware exploration might be in order – for instance, we’ve torn down the Sling Adapter and even ran simple custom code on it!
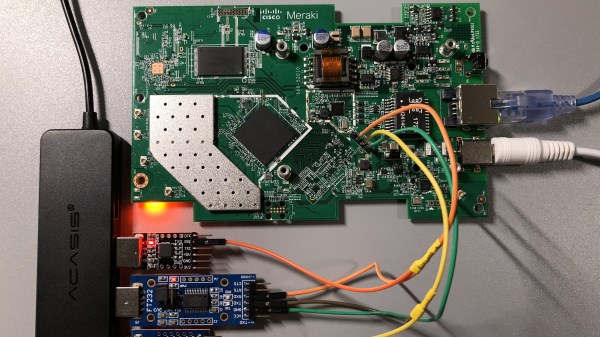
Flashing Booby-Trapped Cisco AP With OpenWrt, The Hard Way
Certain manufacturers seriously dislike open-source firmware for their devices, and this particular hack deals with quite extreme anti-hobbyist measures. The Meraki MR33, made by Cisco, is a nice access point hardware-wise, and running OpenWrt on it is wonderful – if not for the Cisco’s malicious decision to permanently brick the CPU as soon as you enter Uboot through the serial port. This AP seems to be part of a “hardware as a service” offering, and the booby-trapped Uboot was rolled out by an OTA update some time after the OpenWrt port got published.
There’s an older Uboot version available out there, but you can’t quite roll back to it and up to a certain point, there was only a JTAG downgrade path noted on the wiki – with its full description consisting of a “FIXME: describe the process” tag. Our hacker, an anonymous user from the [SagaciousSuricata] blog, decided to go a different way — lifting, dumping and modifying the onboard flash in order to downgrade the bootloader, and guides us through the entire process. There’s quite a few notable things about this hack, like use of Nix package manager to get Python 2.7 on an OS which long abandoned it, and a tip about a workable lightweight TFTP server for such work, but the flash chip part caught our eye.
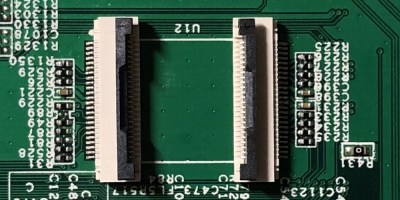 The flash chip is in TSOP48 package and uses a parallel interface, and an iMX6.LL devboard was used to read, modify and flash back the image — hotswapping the chip, much like we used to do with old parallel-interface BIOS chips. We especially liked the use of FFC cables and connectors for connecting the flash chip to the devboard in a way that allows hotswapping – now that we can see it, the TSOP 0.5 mm pitch and 0.5 mm FFC hardware are a match made in heaven. This hack, of course, will fit many TSOP48-equipped devices, and it’s nice to have a toolkit for it in case you don’t have a programmer handy.
The flash chip is in TSOP48 package and uses a parallel interface, and an iMX6.LL devboard was used to read, modify and flash back the image — hotswapping the chip, much like we used to do with old parallel-interface BIOS chips. We especially liked the use of FFC cables and connectors for connecting the flash chip to the devboard in a way that allows hotswapping – now that we can see it, the TSOP 0.5 mm pitch and 0.5 mm FFC hardware are a match made in heaven. This hack, of course, will fit many TSOP48-equipped devices, and it’s nice to have a toolkit for it in case you don’t have a programmer handy.
In the end, the AP got a new lease of life, now governed by its owner as opposed to Cisco’s whims. This is a handy tutorial for anyone facing a parallel-flash-equipped device where the only way appears to be the hard way, and we’re glad to see hackers getting comfortable facing such challenges, whether it’s parallel flash, JTAG or power glitching. After all, it’s great when your devices can run an OS entirely under your control – it’s historically been that you get way more features that way, but it’s also that the manufacturer can’t pull the rug from under your feet like Amazon did with its Fire TV boxes.
We thank [WifiCable] for sharing this with us!
(Ed Note: Changed instances of “OpenWRT” to “OpenWrt”.)
Hackaday Links: April 24, 2022
Wait, what? Is it possible that a tech company just killed off a product with a huge installed base of hardware and a community of dedicated users, and it wasn’t Google? Apparently not, if the stories of the sudden demise of Insteon are to be believed. The cloud-based home automation concern seems to have just disappeared — users report the service went offline at the end of last week, and hasn’t been back since. What’s more, the company’s executives removed Insteon from their LinkedIn profiles, and the CEO himself went so far as to remove his entire page from LinkedIn. The reasons behind the sudden disappearance remained a mystery until today, when The Register reported that Smartlabs, Inc., the parent company of Insteon, had become financially insolvent after an expected sale of the company failed in March. The fact that the company apparently knew this was going to happen weeks ago and never bothered to give the community a heads up before pulling the switches has led to a lot of hard feelings among the estimated 100,000 Insteonhub users.
Then again, with a comet the size of Rhode Island heading our way, a bunch of bricked smart bulbs might just be a moot point. The comet, known as C/2014 UN271, has a nucleus that is far larger than any previously discovered comet, which makes it a bit of an oddball and an exciting object to study. For those not familiar with the United States, Rhode Island is said to be a state wedged between Connecticut and Massachusetts, but even having lived in both those states, we couldn’t vouch for that. For scale, it’s about 80 miles (128 km) across, or a little bit bigger than Luxembourg, which we’re pretty sure is mythical, too. The comet is a couple of billion miles away at this point; it may never get closer than a billion miles from the Sun, and that in 2031. But given the way things have been going these last few years, we’re not banking on anything.
From the “Answering the Important Questions” file, news this week of the Massachusetts Institute of Technology’s breakthrough development of the “Oreometer,” a device to characterize the physical properties of Oreo cookies. The 3D printed device is capable of clamping onto the wafer parts of the popular sandwich cookie while applying axial torque. The yield strength of the tasty goop gluing the two wafers together can be analyzed, with particular emphasis on elucidating why it always seems to stay primarily on one wafer. Thoughtfully, the MIT folks made the Oreometer models available to one and all, so you can print one up and start your own line of cookie-related research. As a starting point, maybe take a look at the shear strength of the different flavors of Oreo, which might answer why the world needs Carrot Cake Oreos.
And finally, since we mentioned the word “skiving” last week in this space, it seems like the all-knowing algorithm has taken it upon itself to throw this fascinating look at bookbinding into our feed. We’re not complaining, mind you; the look inside Dublin’s J.E. Newman and Sons bookbinding shop, circa 1981, was worth every second of the 23-minute video. Absolutely everything was done by hand back then, and we’d imagine that very little has changed in the shop over the ensuing decades. The detail work is incredible, especially considering that very few jigs or fixtures are used to ensure that everything lines up. By the way, “skiving” in this case refers to the process of thinning out leather using a razor-sharp knife held on a bias to the material. It’s similar to the just-as-fascinating process used to make heat sinks that we happened upon last week.
Hackaday Links: November 1, 2020
We normally chuckle at high-profile auctions where people compete to pay as much as possible for items they clearly don’t need. It’s easy to laugh when the items on the block are things like paint-spattered canvases, but every once in a while some genuine bit of history that really piques our interest goes on sale. Such is the case with what is claimed to be an original Steve Wozniak-built Blue Box, going on sale November 5. The prospectus has an excellent summary of the history of the “Two Steves” and their early business venture making and selling these devices to Berkeley students eager to make free long distance phone calls. The item on sale is a very early rev, most likely assembled by Woz himself. The current owner claims to have bought it from Woz himself in the summer of 1972 while on a roadtrip from Sunnyvale to Los Angeles. Estimated to go for $4,000 to $6,000, we really hope this ends up in a museum somewhere — while we’ve seen attempts to recreate Woz’s Blue Box on Hackaday.io, letting a museum study an original would be a great glimpse into our shared technological history.
Not in the market for old tech? No problem — Digilent wants to get rid of 3,000 PCBs, and quickly. They posted the unusual offer on reddit a couple of days ago; it seems they have a huge stock of populated boards for a product that didn’t quite take the market by storm. Their intention is likely not to flood the market with scopes cobbled together from these boards, but rather to make them available to someone doing some kind of art installation or for educational purposes. It’s a nice gesture, and a decent attempt to keep these out of the e-waste stream, so check it out if you have a need.
Speaking of PCBs, SparkFun has just launched an interesting new service: SparkFun À La Carte. The idea is to make it really easy to design and build prototype boards. Instead of using traditional EDA software, users select different blocks from a menu. Select your processor, add components like displays and sensors, and figure out how you want to power it, and SparkFun will do the rest, delivering a fully assembled board in a few weeks. It certainly stands to suck the fun out of the design process while also hoovering up your pocketbook: “A $949 design fee will be applied to all initial orders of a design”. You can get your hands on the design files, but that comes with an extra fee: “they can be purchased separately for $150 by filling out this form”. But for someone who just needs to hammer out a quick design and get on with the next job, this could be a valuable tool.
Another day, another IoT ghost: Reciva Radio is shutting down its internet radio service. A large banner at the top of the page warns that the “website will be withdrawn” on January 31, 2021, but functionality on the site already appears limited. Users of the service are also reporting that their Reciva-compatible radios are refusing to stream content, apparently because they can’t download anything from the service’s back end. This probably doesn’t have a huge impact — I’d never heard of Reciva before — but it makes me look at the Squeezebox radio we’ve got in the kitchen and wonder how long for the world that thing is. It’s not all bad news, though — owners of the bricked radios will now have a great opportunity to hack them back into usefulness.
By the time this article is published, Halloween will be history and the hordes of cosplaying candy-grubbers who served as welcome if ironic respite from this non-stop horror show of a year will be gone. Luckily, though, if it should come to pass that the dead rise from their graves — it’s still 2020, after all — we’ll know exactly how to defeat them with this zombie invasion calculator. You may remember that last year Dominik Czernia did something similar, albeit with vampires. Switching things up from the hemophagic to the cerebrophagic this year, his calculator lets you model different parameters, like undead conversion percentage, zombie demographics, and attack speed. You’ve also got tools for modeling the response of the living to the outbreak, to see how best to fight back. Spoiler alert: everyone will need to bring Tallahassee-level badassery if we’re going to get through this.