There are few production cars with as much geek cred as the DMC DeLorean. If you want to kick the nerdiness up a notch without doing a full Back to the Future prop-mod, then the next best thing is to make it an EV.
[Bill Carlson] took a 1981 DeLorean and transplanted the drivetrain from a Chevy Bolt to electrify this ride. With the DeLorean being a rear wheel drive vehicle and the Bolt front wheel, there was some amount of component reshuffling to do. The motor is now in the rear of the car along with the main contactor, charger, and motor controller while the batteries are split between a pack in the original engine compartment and another up front under the hood.
The electric power steering and brake booster from the Bolt now also live under the hood, and the accelerator and steering column from the EV were transplanted into the cockpit. [Carlson] still needs to tidy up the interior of the car which is currently a nest of low voltage cables as well as add the cooling system which will bring this stainless monster up to a hefty 3200 lbs (~1450 kg) versus the original 2850 lbs (~1300 kg). We suspect the total bill came in a bit lower than getting an electric DeLorean Alpha5.
This isn’t the first electric DeLorean we’ve covered here, and if that isn’t cool enough, how about this DeLorean-inspired hovercraft?





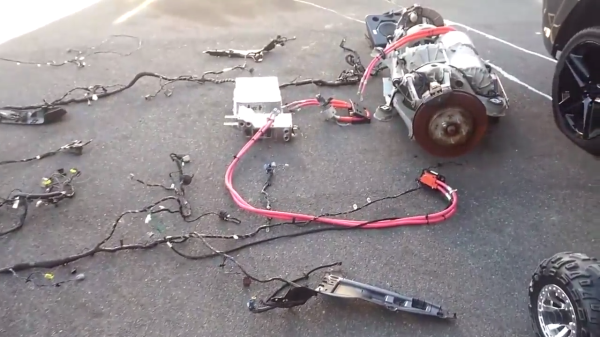
 to strip this car of all such parts, and sell what he could to recover the cost of his initial purchase. After selling the working modules of the otherwise drenched battery, motor and a few other bells and whistles his initial monetary investment was reduced to the mere investment of time.
to strip this car of all such parts, and sell what he could to recover the cost of his initial purchase. After selling the working modules of the otherwise drenched battery, motor and a few other bells and whistles his initial monetary investment was reduced to the mere investment of time.










