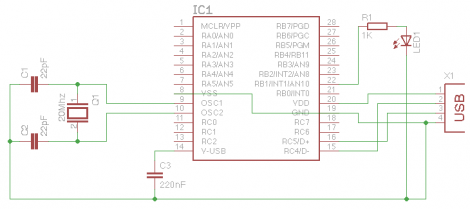
There’s now a method of using PIC microcontrollers to exploit the PlayStation 3. This is centered around a PIC 18F2550 which has been popular in past hacks because of its built-in USB serial port. This again makes use of the PSGroove open source exploit code and, like the TI calculator version, seeks to expand the selection of hardware the code runs on.
In addition to the chip and a PIC programmer you’ll need the CCS compiler as others cannot successfully compile this code. A licensed copy is necessary because the demo version of the CCS compiler doesn’t support this particular chip. Add to that the fact that because of the timing it may take several tries to achieve the exploit and you may find yourself disappointed by this development. But there’s always room for improvement and this is a proven first step on the new architecture.
[Thanks das_coach via PS3Hax via Elotrolado]
















