People who exercise with fitness trackers have a digital record of their workouts. They do it for a wide range of reasons, from gathering serious medical data to simply satisfying curiosity. When fitness data includes GPS coordinates, it raises personal privacy concerns. But even with individual data removed, such data was still informative enough to spill the beans on secretive facilities around the world.
Strava is a fitness tracking service that gathers data from several different brands of fitness tracker — think Fitbit. It gives athletes a social media experience built around their fitness data: track progress against personal goals and challenge friends to keep each other fit. As expected of companies with personal data, their privacy policy promised to keep personal data secret. In the same privacy policy, they also reserved the right to use the data shared by users in an “aggregated and de-identified” form, a common practice for social media companies. One such use was to plot the GPS data of all their users in a global heatmap. These visualizations use over 6 trillion data points and can be compiled into a fascinating gallery, but there’s a downside.
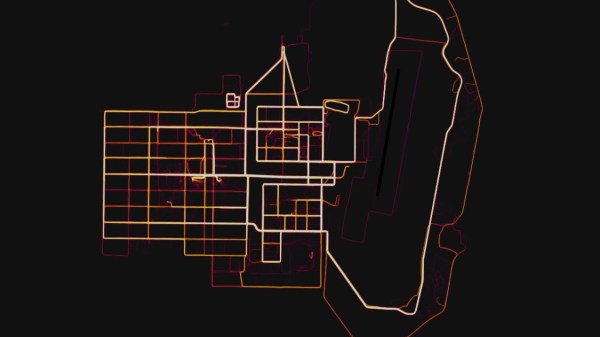
This past weekend, [Nathan Ruser] announced on Twitter that Strava’s heatmap also managed to highlight exercise activity by military/intelligence personnel around the world, including some suspected but unannounced facilities. More worryingly, some of the mapped paths imply patrol and supply routes, knowledge security officers would prefer not to be shared with the entire world.
This is an extraordinary blunder which very succinctly illustrates a folly of Internet of Things. Strava’s anonymized data sharing obsfucated individuals, but didn’t manage to do the same for groups of individuals… like the fitness-minded active duty military personnel whose workout habits are clearly defined on these heat maps. The biggest contributor (besides wearing a tracking device in general) to this situation is that the data sharing is enabled by default and must be opted-out:
“You can opt-out of contributing your anonymized public activity data to Strava Metro and the Heatmap by unchecking the box in this section.” —Strava Blog, July 2017
We’ve seen individual fitness trackers hacked and we’ve seen people tracked through controlled domains before, but the global scope of [Nathan]’s discovery puts it in an entirely different class.
[via Washington Post]

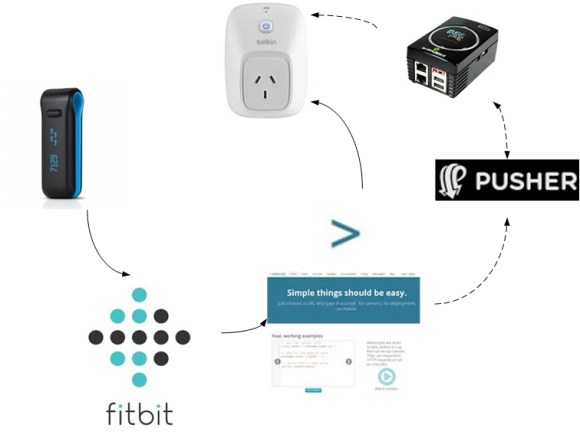
 Data begin sent between the Fitbit and the phone can be encrypted, but there is a live mode that sends the data as plain text. The implementation seemed to be security by obscurity as a new Bluetooth handle is used for this mode. This technique prevents the need to send every encrypted packet to the server for decryption (which would be for every heartbeat packet). So far the fix for this has been the ability to disable live mode. If you have your own Fitbit to play with, sniffing live mode would be a fun place to start.
Data begin sent between the Fitbit and the phone can be encrypted, but there is a live mode that sends the data as plain text. The implementation seemed to be security by obscurity as a new Bluetooth handle is used for this mode. This technique prevents the need to send every encrypted packet to the server for decryption (which would be for every heartbeat packet). So far the fix for this has been the ability to disable live mode. If you have your own Fitbit to play with, sniffing live mode would be a fun place to start.