Ever want to get into reverse engineering but don’t know where to start? You’re in luck — [Hash] just dropped a case study in chip glitching that should get you off on the right foot.
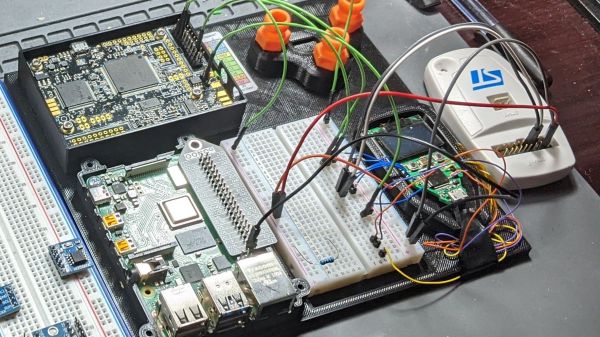
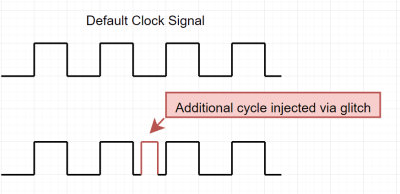
The object of this reverse engineering effort in the video below is a Microchip SAM4C32C, removed from one of the many smart electrical meters [Hash] loves to tear into. This microcontroller was supposed to be locked to prevent anyone from sniffing around in the code, but after soldering the chip to a target board and plugging it into a Chip Whisperer, [Hash] was able to find some odd-looking traces on the oscilloscope. Of particular interest was an unusual pattern on the scope while resetting the chip, which led him to an AI-assisted search for potential vulnerabilities. This allowed him to narrow down the target time for a power glitch, and in only a few seconds, the chip was forced to bypass its security bit and drop into its boot loader. With the keys to the kingdom, [Hash] was able to read the firmware and find all sorts of interesting tidbits.
Obviously, chip glitching isn’t always as easy as this, and even when a manufacturer leaves a vector like this in the chip, exploiting it does take some experience and finesse. But, if you’re going to get started glitching, it makes sense to start with the low-hanging fruit, and having [Hash] along for the ride doesn’t hurt either.