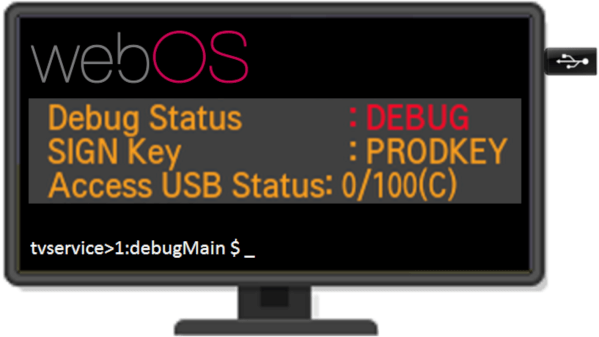
One boring evening, [XenRE] was looking through service menus on their LG Smart TV (Russian, Google Translate), such menus accessible through use of undocumented IR remote codes. In other words, a fairly regular evening. They noticed an “Access USB Status” entry and thought the “Access USB” part looked peculiar. A few service manuals hinted that there’s a service mode you could access with an adapter made out of two back-to-back PL2303 USB-UART adapters – a few female-female jumper wires later, serial prompt greeted our hacker, and entering ‘debug’ into the prompt responded with some text, among it, “Access USB is NOT opened!!!”.
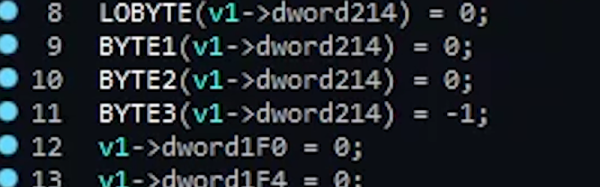
[XenRE] found the WebOS firmware for the TV online, encrypted and compressed into a proprietary LG .epk format, but liberated with an open-source tool. A few modules referred to AccessUSB there, and one detour into investigating and explaining WebOS USB vendor lock-in implementation later, they programmed an STM32 with the same VID and PID as the mythical AccessUSB device found in relevant WebOS modules decompiled with IDA. By this point, AccessUSB could safely be assumed to be a service mode dongle. The TV didn’t quite start beeping in a different pattern as we’d expect in a sci-fi movie, but it did notify about a “new USB device” – and started asking for a 6-symbol service menu password instead of a 4-symbol one. Continue reading “What’s That AccessUSB Menu In My LG SmartTV?”