The month or so after the holidays have always been a great time to pick up some interesting gadgets on steep clearance, but with decorations and lights becoming increasingly complex over the last few years, the “Christmas Clearance” rack is an absolute must see for enterprising hackers. You might just luck out like [ModernHam] and find a couple packs of these dirt cheap wireless light controllers, which can fairly easily be hacked into the start of a home automation system with little more than the Raspberry Pi and a short length of wire.
In the video after the break, [ModernHam] walks the viewer through the start to finish process of commanding these cheap remote plugs. Starting with finding which frequencies the remotes use thanks to the FCC database and ending with using cron to schedule the transmission of control signals from the Pi, his video really is a wealth of information. Even if you don’t have this particular model of remote plug, or don’t necessarily want to setup a home automation system, there’s probably some element of this video that you could still adapt to your own projects.
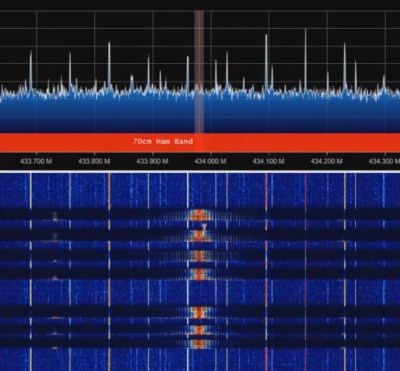 The first step of the process is figuring out how the remote is communicating to the plugs. [ModernHam] noticed there was no frequency listed on the devices, but using their FCC IDs he was able to find the relevant information. In the United States, devices like these must have their FCC IDs visible (though they could be behind a battery door) by law, so the searchable database is an invaluable tool to do some basic reconnaissance on a poorly documented gadget.
The first step of the process is figuring out how the remote is communicating to the plugs. [ModernHam] noticed there was no frequency listed on the devices, but using their FCC IDs he was able to find the relevant information. In the United States, devices like these must have their FCC IDs visible (though they could be behind a battery door) by law, so the searchable database is an invaluable tool to do some basic reconnaissance on a poorly documented gadget.
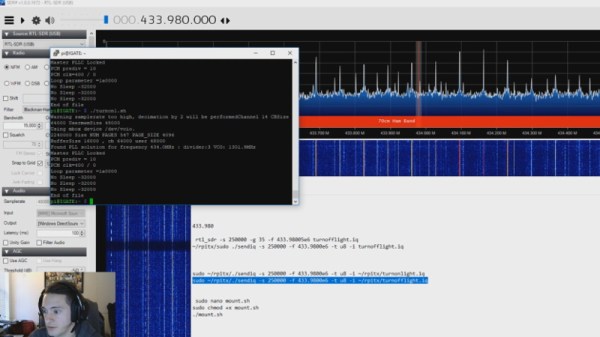
An RTL-SDR receiver is then used to fine tune the information gleaned from the FCC filing. [ModernHam] found that the signals for all four of the remote plugs were being broadcast on the same frequency, which makes controlling them all the easier. Using the rtl-sdr command, he was able to capture the various signals from the transmitter and save them to separate files. Then it’s just a matter of replaying the appropriate file to get the plugs to do your bidding.
Of course, the RTL-SDR can’t transmit so you’ll have to leave your dongle behind for this last step. Luckily all you need to transmit is the rpitx package created by [F5OEO], along with a supported Raspberry Pi and a small length of wire attached to the appropriate GPIO pin. This package contains the tool sendiq which can be used to replay the raw captures made in the previous step. With some scripting, it’s fairly straightforward to automate these transmissions to control the remote plugs however you wish from the Pi.
The RTL-SDR Blog put together their own guide for “brute forcing” simple remote control devices like this as well, and we’ve even seen similar techniques used against automotive key fobs in the past. Amazing what a piece of wire and some clever code can pull off.
Continue reading “Automate Your Home From The Clearance Rack” →