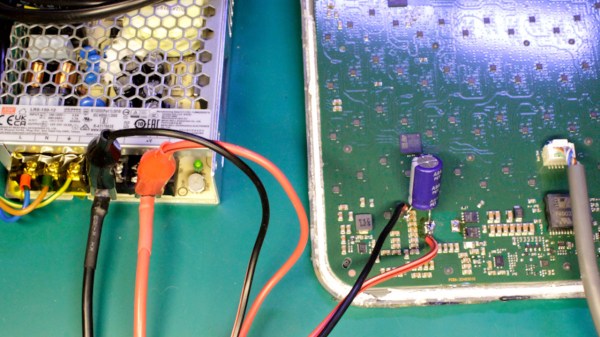
Sometimes, you will want to power a device in a way it wasn’t designed for, and you might find that the device in question is way too tailored to the original power source. Today, [Oleg Kutkov] is here to give us a master class on excising unnecessary power conversion out of your devices, with the Starlink terminal as an example. This device can only be officially powered from 48V PoE, but can technically work from about 12V – and, turns out, many people want to mount a Starlink terminal to their cars.
[Oleg] shows us the power circuit of the Starlink terminal, explaining which component is responsible for what, and gives us a block diagram. Then, he shows you the 12V rail that all internal components actually draw power from, and where to feed power into it. Plus, he warns you about possible caveats, like having to disable the builtin 12V regulator to prevent it from backfeeding-induced damage. If you’re looking to modify a similar device, this tutorial gives you heaps of insight on what you might need on your foray.
Thinking to modify your own Starlink terminal, perhaps, and wondering about the power consumption? [Oleg] has current consumption graphs for you, collected with a data logger for Uni-T UT800 of his own design, providing detailed figures on just how much energy you ought to supply to power the terminal from 12V, and where to (not) get it. After all, even a seemingly suitable power supply might not do.