As 3D printing becomes more and more used in a wide range of fields, medical science is not left behind. From the more standard uses such as printing medical equipment and prosthetics to more advanced uses like printing cartilages and bones, the success of 3D printing technologies in the medical field is rapidly growing.
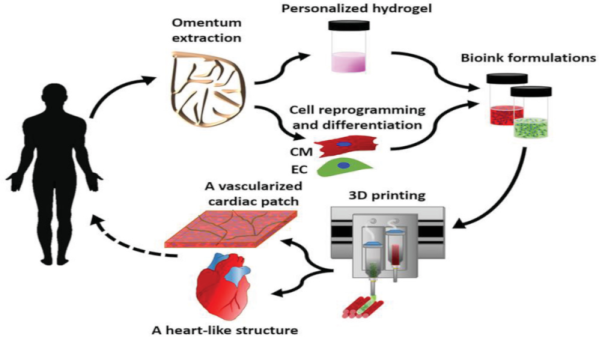
One of the last breakthrough is the world’s first 3D vascularised engineered heart using the patient’s own cells and biological materials. Until now, scientists have only been successful in printing only simple tissues without blood vessels. Researchers from Tel Aviv University used the fatty tissue from patients to separate the cellular and acellular materials and reprogrammed the cells become pluripotent stem cells. The extracellular matrix (ECM) was processed into a personalized hydrogel that served as the basis from the print.
This heart is made from human cells and patient-specific biological materials. In our process these materials serve as the bioinks, substances made of sugars and proteins that can be used for 3D printing of complex tissue models… At this stage, our 3D heart is small, the size of a rabbit’s heart, but larger human hearts require the same technology.
After being mixed with the hydrogel, the cells were efficiently differentiated to cardiac or endothelial cells to create patient-specific, immune-compatible cardiac patches with blood vessels and, subsequently, an entire heart that completely matches the immunological, cellular, biochemical and anatomical properties of the patient. The difficulty of printing full-blown organs were being tackled for a long time and we already talked about it in the past.
The development of this technology may completely solve both the problem of organ compatibility and organ rejection.