Android, the popular mobile phone OS, is essentially just Linux with a nice user interface layer covering it all up. In theory, it should be able to do anything a normal computer running Linux could do. And, since most web servers in the world are running Linux, [PelleMannen] figured his Android phone could run a web server just as well as any other Linux machine and built this webpage that’s currently running on a smartphone, with an additional Reddit post for a little more discussion.
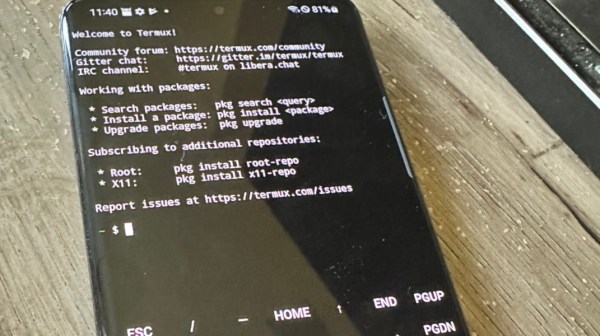
The phone uses Termux (which we’ve written about briefly before) to get to a Bash shell on the Android system. Before that happens, though, some setup needs to take place largely involving installing F-Droid through which Termux can be installed. From there the standard SSH and Apache servers can be installed as if the phone were running a normal Linux The rest of the installation involves tricking the phone into thinking it’s a full-fledged computer including a number of considerations to keep the phone from halting execution when the screen locks and other phone-specific issues.
With everything up and running, [PelleMannen] reports that it runs surprisingly well with the small ARM system outputting almost no heat. Since the project page is being hosted on this phone we can’t guarantee that the link above works, though, and it might get a few too many requests to stay online. We wish it were a little easier to get our pocket-sized computers to behave in similar ways to our regular laptops and PCs (even if they don’t have quite the same amount of power) but if you’re dead-set on repurposing an old phone we’ve also seen them used to great effect in place of a Raspberry Pi.