Want to hack on brand new 8-bit 1980s hardware? Until recently you needed a time machine, or deep pockets to do this. All that has recently changed with the NABU PC. A retro machine that can be bought brand new for $59.99, (plus shipping) no time machine needed.
[Adrian] has one in his Digital Basement, and breaks it all down for us. The NABU PC was a Canadian computer. Designed to connect to the cable TV network, the standard system had no internal secondary storage. You read that right; the NABU used the cable network to download and play games, view documents — just about anything you’d want to do with a computer. Cable modems back in the 80s — maybe someone did have a time machine?
Unfortunately, the NABU network failed. Not due to the PC’s hardware, but because the cable system back then was not designed for bidirectional data. While the NABU PC did see a limited release in Canada, was never widely successful. When production was shut down, the machines couldn’t be liquidated, as they didn’t do anything without the network. So in the warehouse, they sat, until this month, where can find them being sold on eBay.
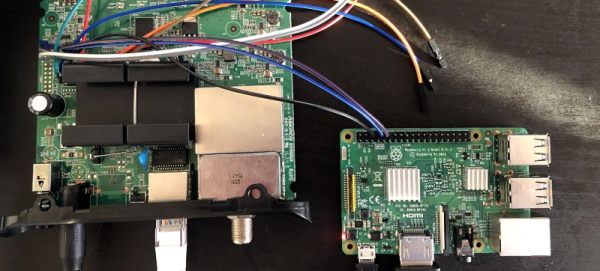
So what’s inside a NABU? It starts with a Z-80 CPU sporting 64 kB of RAM. A TMS9918 handles video, while a General Instrument AY-3-8910 does the sound. There are also two UARTs. An 8251 for serial io to the keyboard and joysticks, and a high-performance UART chip to handle comms with the network adapter. The keyboard is loaded with good old ALPS switches, and [Adrian] found it rather impressive.
That’s all well and good, but what can you actually do with a NABU PC? Right now, not much. The ROM software comes up and looks for the network adapter, then complains when it doesn’t find it. This means it’s hacking time! An army of retrocomputing enthusiasts are already working on bringing back the NABU computer. Check [Adrian]’s video description for all the documentation links, and check here on Hackaday for the latest updates!
This isn’t our first time watching this sort of liquidation — remember the HP touchpad?
Continue reading “NABU PC – A 1984 Z-80 Computer You Can Buy Today”