Spending an hour or two around any consumer-level padlock or house deadbolt lock with a simple lockpicking kit will typically instill a good amount of panic and concern about security. While it’s true that any lock can be defeated, it’s almost comically easy to pick basic locks like this. So, if you’re looking for a level of security that can’t be defeated in two minutes with a tiny piece of metal, you might want to try something a little more advanced.
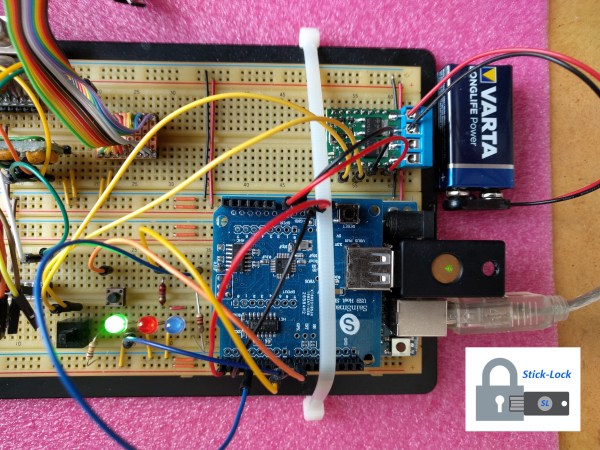
This project stemmed from an idea to use a YubiKey, a USB hardware token typically used for two-factor authentication, for physical locks instead. The prototype was built around an Arduino UNO, and all of the code and build instructions are available on the project’s site. The creator, [rprinz08], does not have one built inside of a secure enclosure so that would remain an exercise for the reader, but the proof-of-concept is interesting and certainly useful.
While digital keys like this can have their own set of problems (as all locks do), this would be a great solution for anyone needing to lock up anything where physical keys are a liability or a nuisance, where logging is important, or where many people need access to the same lock. The open source code and well-known platform make it easy for anyone to build, too.