[youtube=http://www.youtube.com/watch?v=VgfyUsjwGwM&hl=en&fs=1&rel=0&color1=0x3a3a3a&color2=0x999999]
If you feel that your iPhone alone no longer carries the cachet it once did, what with the price dropping and all, this may be just the modification that you need to stand out among the crowd. iPhones.ru has a teaser glimpse of an iPhone hack that causes the Apple logo on the back of the device to light up when the screen is turned on. Details are sketchy, but it appears that the hack involves replacing the metal insert on the back of the phone with an LED-equipped plastic one; custom software allows the user to select the brightness of the glowing effect independently of screen brightness… or maybe they’re just using the backlight.
Day: August 15, 2008
Biometric Locks Turned Trojan

In the same vein as our recent Defcon article on biometric cloning, White Wolf Security has released this article about turning a biometric door lock into a trojan. They note that there are many common ways to break into one, from harvesting fingerprints to using gummy bears to fake a finger. This hack involves having full access to the unit so you can disassemble it.
The unit has a system built-in where you can touch a 9-volt battery to some connectors on the bottom to power it in case of a building power failure. The researchers simply routed some wires from the motorized lock to the plates used for the 9-volt and then reassembled the lock. The door can then be opened at any time without verification, even if the software on the unit is reset.
[Thanks, dwight]
Robot That Runs On Rat Brain Cells
Scientists at the University of Reading have created a robot that runs not on microprocessors, but on brain cells extracted from a rat fetus. The robot is equipped with several sensors which stimulate the rat neurons whenever the robot approaches a wall; the response of the neurons then determines whether the robot avoids the wall or crashes into it. The truly fascinating bit is that the rat brain cells don’t automatically know how to respond to the stimuli from the sensors, but instead learn to respond appropriately through repeated stimuli.
No word yet on whether the scientists will teach the robot to sing “Despite all my rage / I am still just a brain in a vat”.
Make A Stretchy Fabric USB Cable
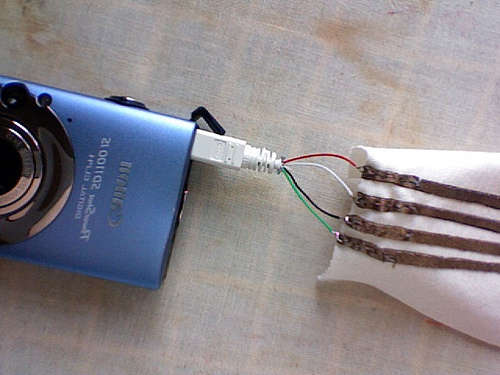
If you’ve been puzzled over a discreet, durable way to sew wiring into your clothing, then puzzle no more: [Plusea] has put together a writeup detailing how to make a USB cable partly out of stretchy cotton fabric. Although the design as detailed doesn’t give much practical use for the invention, we can think of several very effective ways of exploiting this toy. Imagine, for example, placing a USB battery pack into one pocket of a jacket, a portable digital audio recorder in the other, and a lavalier microphone in the lining, thus enabling dozens of hours of covert audio surveillance.










