The stereotypical hardware hacker is a creature of the night. Some of us do our best work in the wee hours. The unfortunate side effect of this is that we have a hard time getting up in the morning. Sometimes life demands a hacker be up-and-at-em before noon though. In these cases, the only solution is an alarm clock. This week’s Hacklet features some of the best alarm clock projects on Hackaday.io!
 We start with [hberg32] and Merciless Pi Alarm Clock. Merciless is a good name for this Raspberry Pi based clock. We have to say it’s quite snazzy with its laser cut case and large seven segment LED face. When the alarm goes off though, this Pi bites back.
We start with [hberg32] and Merciless Pi Alarm Clock. Merciless is a good name for this Raspberry Pi based clock. We have to say it’s quite snazzy with its laser cut case and large seven segment LED face. When the alarm goes off though, this Pi bites back.
Titanium drivers powered by a 20 watt amplifier will wake even the heaviest sleepers. If that’s not enough, [hberg32] added a bed shaker to vibrate you out of the sack. The snooze button only works 3 times, after that you can press all you want, the music will still play. As if that wasn’t enough, this clock even has a pressure sensor. If you get back in bed, the alarm starts up again. Truly fitting of the name “merciless”.
 [Ceady] took the kinder, gentler route with Integrated Room Sunrise Simulator. This alarm clock simulates dawn, gently waking the user up. A Lutron Maestro series wireless dimmer allows the sunrise simulator to slowly increase the room’s light level over a period of 10 minutes, allowing [Ceady] to wake up silently.
[Ceady] took the kinder, gentler route with Integrated Room Sunrise Simulator. This alarm clock simulates dawn, gently waking the user up. A Lutron Maestro series wireless dimmer allows the sunrise simulator to slowly increase the room’s light level over a period of 10 minutes, allowing [Ceady] to wake up silently.
The clock itself uses an ATmega168 for control. [Ceady] spent a considerable amount of time testing out different methods of creating a seven segment LED display. When casting with cornstarch and resin didn’t do the trick, he went to commercial LED diffuser film from Inventables. The film proved to be just what he was looking for.
 Next up is [Spiros Papadimitriou] with DIY Chumby-lite. Taking inspiration from [Bunnie Huang] and the Chumby project, [Spiros] created a friendly alarm clock with a touchscreen LCD. Much like the Chumby, this clock packs a WiFi module.
Next up is [Spiros Papadimitriou] with DIY Chumby-lite. Taking inspiration from [Bunnie Huang] and the Chumby project, [Spiros] created a friendly alarm clock with a touchscreen LCD. Much like the Chumby, this clock packs a WiFi module.
In this case though, the WiFi module is an ESP8266, whose on-board Xtensa microcontroller runs the whole show. [Spiros] programmed his Sparkfun ESP8266 Thing in C++. To keep costs down, [Spiros] left out anything unnecessary – like a real-time clock module. The Chumby-lite uses NTP to stay regular. The reductions paid off – this clock can be built for around $13.00, not including the very nice 3D printed case.
 [Wanderingmetalhead] takes us all way back to 1983 with his 7 Day Alarm Clock. 32 years ago, this was [wanderingmetalhead’s] first embedded system project. As the name implies, this clock stores a different wake time for each day of the week. Actual numeric entry sure beats the old “hold two buttons and watch the numbers spin” system.
[Wanderingmetalhead] takes us all way back to 1983 with his 7 Day Alarm Clock. 32 years ago, this was [wanderingmetalhead’s] first embedded system project. As the name implies, this clock stores a different wake time for each day of the week. Actual numeric entry sure beats the old “hold two buttons and watch the numbers spin” system.
This is an oldie. The system is based upon a Motorola (which became Freescale, and is now NXP) 6802 micro. The code was written in assembly and cross-assembled on an Apple II. A 3.58MHz colorburst crystal divided down to 60 Hz provides the time base. This setup wasn’t perfect, but good down to a about a minute a month. The whole project lived and worked in an old amplifier case, where it dutifully woke [wanderingmetalhead] each day for 17 years.
If you want to see more alarm clock projects, check out our new alarm clocks list! If I didn’t wake up early enough to catch your project, don’t be shy, just drop me a message on Hackaday.io. That’s it for this week’s Hacklet. As always, see you next week. Same hack time, same hack channel, bringing you the best of Hackaday.io!




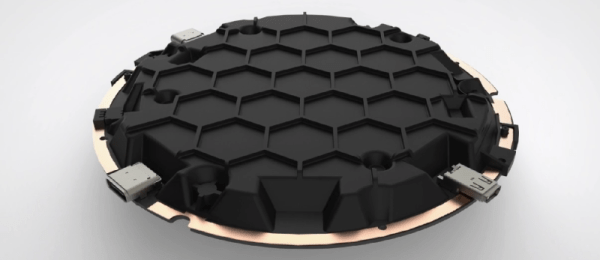
 The big draw to the ORWL is a ‘honeycomb mesh’ that completely covers every square inch of circuit board. This honeycomb mesh is simply a bit of plastic that screws on to the ORWL PCB and connects dozens of electronic traces embedded in this board to a secure microcontroller. If these traces are broken – either through taking the honeycomb shell off or by breaking it wide open, the digital keys that unlock the computer are erased.
The big draw to the ORWL is a ‘honeycomb mesh’ that completely covers every square inch of circuit board. This honeycomb mesh is simply a bit of plastic that screws on to the ORWL PCB and connects dozens of electronic traces embedded in this board to a secure microcontroller. If these traces are broken – either through taking the honeycomb shell off or by breaking it wide open, the digital keys that unlock the computer are erased.