What’s more expensive than a car and a less useful means of transportation? A 747 flight simulator built in a basement. There’s a project page where a few more details are revealed. There’s a 180 degree wrap-around screen for the main display, a glass cockpit, and the controls and gauges are ‘good enough’ to feel like the real thing. The simulator is running a highly customized version of FS9 (Microsoft’s flight sim from the year 2004).
For the last few years, Google has been experimenting with high altitude balloons delivering Internet to remote populations. This is Project Loon, and simply by the fact that Google hasn’t shuttered this Alpha-bit, we can assume the project is a success. A Project Loon balloon recently crashed in Panama, which means we can get an up-close look at the hardware. These balloon base stations are a lot bigger than you would think.
We’ve seen beautiful PCBs before, but [Blake] is taking this to another level entirely. He’s developed a process to convert bitmaps into files suitable to send to a PCB manufacturer. The results are… strange, and very cool. Check out a video of the process here.
If you want to dial out from behind the great firewall of China, you’re probably going to use a VPN. Here’s an idea that doesn’t work as well as a VPN. Use an acoustic coupler with your iPhone. Will it work? Of course it will – modems have been standardized for fifty years. Will it work well? No, I can speak faster than 300 baud.
Do you sell on Tindie? We have a dog park. Tindie sellers around the world will be meeting up on Hackaday.io next Friday to discuss Tindie and Tindie-related activities. Join in!
A quick aside relating to Hackaday and Tindie swag. 1) The Tindie dog as a stuffed animal. 2) A Hackaday logo t-shirt where the skull is decorated like a Día de Muertos sugar skull. Pick one, leave your response in the comments.


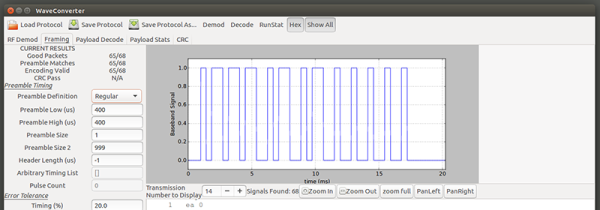
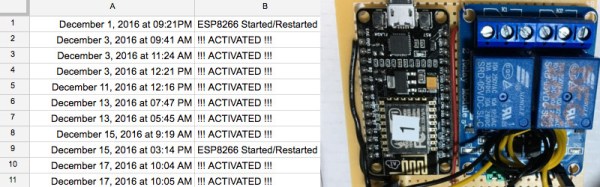
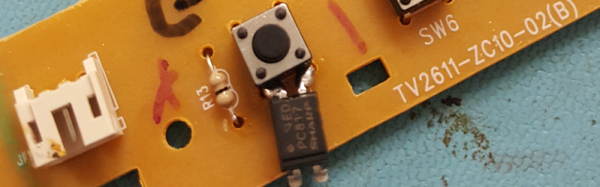
 His victim TV didn’t have the ability to be switched on and off by the Raspberry Pi using HDMI/CEC, so he came up with an alternative. He got a couple of opto-isolators and soldered one to the on/off button on the TV’s control board. The Pi didn’t know whether it was switching the TV on or off, it just knew it was switching it. To solve this, [Troy Denton] connected another opto-isolator to the TV’s LED, this one the other way around. When the TV is turned on, the Pi now detects it.
His victim TV didn’t have the ability to be switched on and off by the Raspberry Pi using HDMI/CEC, so he came up with an alternative. He got a couple of opto-isolators and soldered one to the on/off button on the TV’s control board. The Pi didn’t know whether it was switching the TV on or off, it just knew it was switching it. To solve this, [Troy Denton] connected another opto-isolator to the TV’s LED, this one the other way around. When the TV is turned on, the Pi now detects it.