The Intel 8085 microprocessor was introduced 40 years back, and along with its contemporaries — the Z80 and the 6502 — is pretty much a dinosaur in terms of microprocessor history. But that doesn’t stop it from still being included in the syllabus for computer engineering students in many parts of the world. The reason why a 40 year old microprocessor is still covered in computer architecture text books instead of computer history is a bit convoluted. But there’s a whole industry that thrives on the requirements of college laboratories and students requiring “8085 Microprocessor Training Kits”. [TisteAndii] just finished college in Nigeria, where these kits are not locally built and need to be imported, usually costing well over a 100 dollars.
Which is why his final year project was a low cost Intel 8085 Microprocessor Trainer. It’s a minimalist design with some basic read/write memory, program execution and register inspection, with no provision for single stepping or interrupts yet. The monitor program isn’t loaded in an EEPROM. Instead, a PIC18 is used and connected to the 8085 address, data and control pins. This makes it easier to write a monitor program in C instead of assembly. And allows use of a 1.8″ LCD with SPI interface instead of the more usual 7-segment displays used for these kind of kits. [TisteAndii] built a 6×4 keyboard for input, but couldn’t solve debounce issues and finally settled on a 5×4 membrane keypad.
Being a rookie, he ended up with a major flaw in his board layout — he missed connecting the SRAM and the PPI devices to the data bus. A bunch of jumper links seemed to solve the issue, but it wasn’t perfect. This, and a few other problems gave him a lot of grief, but towards the end, it all worked, almost. Most importantly, his BoM cost of about $35 makes it significantly cheaper compared to the commercial units available in Nigeria.
While some hackers may consider this a trivial project, it solves a local problem and we hope the next iteration of the design improves the kit and makes it more accessible.



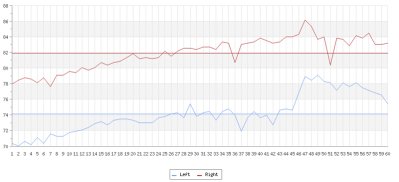

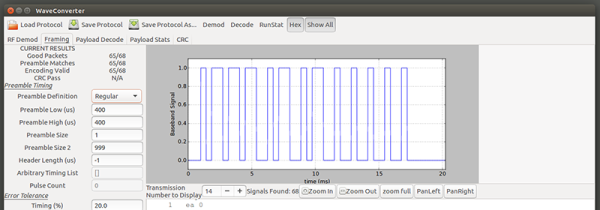
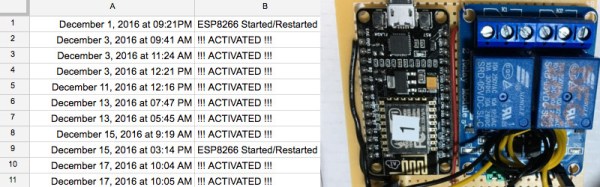
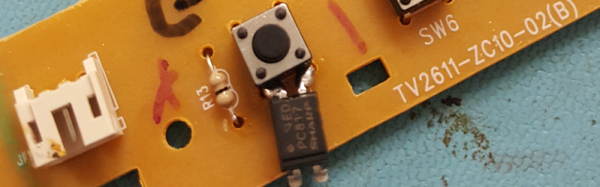
 His victim TV didn’t have the ability to be switched on and off by the Raspberry Pi using HDMI/CEC, so he came up with an alternative. He got a couple of opto-isolators and soldered one to the on/off button on the TV’s control board. The Pi didn’t know whether it was switching the TV on or off, it just knew it was switching it. To solve this, [Troy Denton] connected another opto-isolator to the TV’s LED, this one the other way around. When the TV is turned on, the Pi now detects it.
His victim TV didn’t have the ability to be switched on and off by the Raspberry Pi using HDMI/CEC, so he came up with an alternative. He got a couple of opto-isolators and soldered one to the on/off button on the TV’s control board. The Pi didn’t know whether it was switching the TV on or off, it just knew it was switching it. To solve this, [Troy Denton] connected another opto-isolator to the TV’s LED, this one the other way around. When the TV is turned on, the Pi now detects it.









